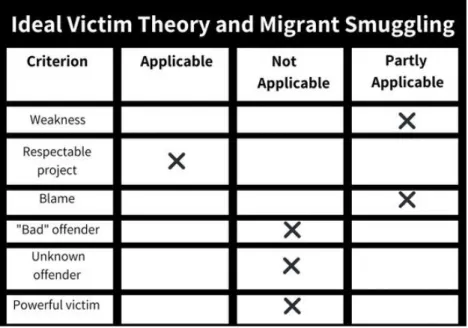
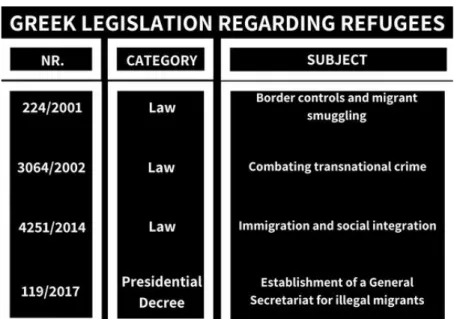
Migrant Smugglers and ICT in Greece
Full text
Figure




Related documents
As jobs were cut, said Irvine real estate consultant Walter Hahn, employees either followed work to places such as Texas, Montana, Idaho and Utah “or they just stopped
The second group (the second quadrant) under the code “Y” is a group with pod cavity diameter and number of superior seeds, but not for pod fresh weight and dry weight per cocoa
The rightmost column of Table III reports returns of the betting-against-beta (BAB) factor of Equation (9), that is, a portfolio that is long a levered basket of low-beta stocks
When connecting to a USB hub, be sure to connect the scanner to the hub nearest to your computer (first stage). If you connect it to a USB hub from the second stage onwards,
This paper uses the liberalisation of the British retail electricity (and gas) industries to examine how these predictions compare to the development of oligopolistic
[r]
The volume of data exchanged and value-added services accessed via in-car Internet will rise significantly by the year 2015 – there is growing demand for
Therefore, based on the literature we argue that resources and capabilities which are possessed by the organization –in this case supply chain connectivity and supply chain