A SURVEY ON VARIOUS AUTHENTICATION TECHNIQUES AND GRAPHICAL PASSWORDS
Full text
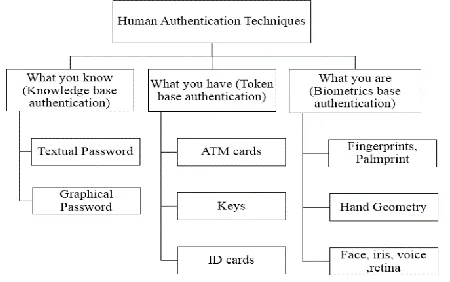
Figure



Related documents
Background: The predictors of shunt dependency such as amount of subarachnoid blood, acute hydrocephalus (HC), mode of aneurysm repair, clinical grade at admission and cerebro
The objective of this study is to identify the local pattern of expenditure on food consumption, dietary habits during Ramadan and correlate that to self- reported weight gain
The Commission concluded also that the online search advertising restrictions and the online sales restrictions had the object of restricting active or passive sales to end users
Employing the use-case of the GOALS online diabetes prevention program, we performed a qualitative study to characterize the preferences of providers concerning the integration
dissemination of patient education publications targeting this population that contained deceptive statements about the risks of addiction and the adverse effects of opioids, and
developed technology , which was first developed in Netherlands and generated electricity from the microbial solar cells (MSC).In this system plants absorbs
Before satellite estimations of precipitation began, global estimates of the distribution of rainfall – essential for characterizing the global water and energy budgets –
This study takes existing research a step further by defining the racial socialization process for African Americans in terms of the impact of parents‟ lived experiences