Efficient and Secure Data Access Control for Multi-Authority Cloud Storage Systems
Full text
Figure
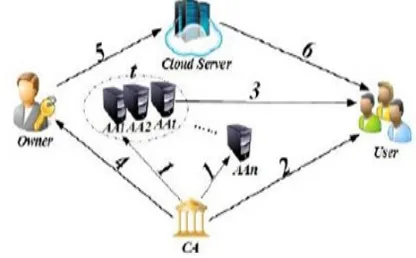
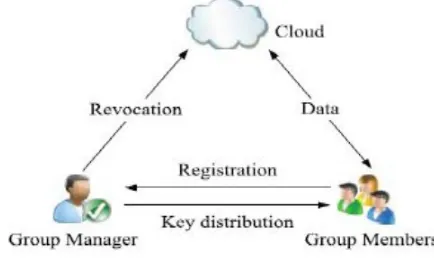
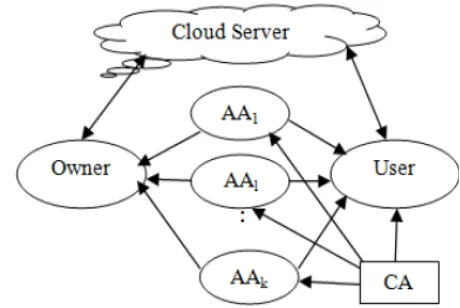
Related documents
• Address: The string of nucleotides representing the data to be put away is broken into data hinders, whose length relies upon the coveted strand length and the
Studies reveals that in Indian SC the most deciding factor in addition to the coordination mechanisms such as SC contracts, Information Technology, Information
Here, we used trait-correlated expression analysis, screening for expression quantitative trait loci (eQTL), genome-wide association (GWA) studies, and causality modeling to
In the final story in The Toughest Indian in the World , Alexie is fully aware of the problems he has pointed out in his other stories in the volume and sets out to begin
Final thesis version The role of Organizational justice in the relationship between LMX, Organizational Commitment and Intent to turnover Amna Yousaf M Sc Thesis University of
Open building case studies were primarily used to compare and contrast various approaches and summarise the best design strategies for high rise living.. There
a) To develop profile of contractual claim in term of head of claim, causes of claim, type of project, parties involved, standard form of contract, time of