An introduction to the Malware Protection Center
Understanding Anti-Malware
Research and Response at Microsoft
Understanding Anti-Malware
Research and Response at Microsoft
Understanding Anti-Malware Research and Response at Microsoft
The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication.This White Paper is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photo copying, recording, or otherwise), or for any purpose, without the express written permission of Microsoft Corporation.
Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property.
© 2007 Microsoft Corporation. All rights reserved.
Microsoft, Forefront, OneCare, Windows, and Hotmail are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries.
The names of actual companies and products mentioned herein may be the trademarks of their respective owners.
Table of Contents
Understanding the Anti-Malware Landscape 1
Microsoft Malware Protection Center . . . . 1
Key Malware Trends 2
Overview of the Microsoft Malware Protection Center 3
Key Response Highlights 5
Global Organization . . . . 6
Advanced Telemetry . . . . 8
Rapid Response . . . . 9
Forward Strategy and Vision 10
Near-Term Strategy . . . . 10
Future Vision . . . . 11
Concluding Thoughts 12
Understanding Anti-Malware Research and Response at Microsoft
Understanding the Anti-Malware Landscape
Viruses, Trojans, and other malicious software, as well as spyware and potentially unwanted software, are a constant concern for IT professionals. The use of social engi neering continues to rise as an attack method, and threats are becoming increasingly sophisticated in their attempts to infect a system. The attacker’s focus has expanded to include the user, often with the intent of stealing financial or other confidential information. Given this frequently changing malware landscape, it is critical to have a well-defined methodology and process for responding to emerging threats.
Effective antimalware protection requires layered security at the network, gateway, application, and operating system levels. Microsoft® has thus developed security solu
tions for both businesses and consumers across these areas that help protect information and control access. Microsoft antimalware solutions are backed by specialized technol ogy, teams, and processes, in particular:
Microsoft Malware Protection Engine: The core software responsible for scan ning, detecting, and removing threats based on malware definitions (discussed in a previous white paper, Understanding Anti-Malware Technologies).
Microsoft Malware Protection Center: The team responsible for proactively investigating new malware and providing rapid response to customers.
This report focuses on the role and activities of the Microsoft Malware Protection Center and its vision to provide thorough, ongoing malware research and response for customers.
Microsoft Malware Protection Center
The Microsoft Malware Protection Center is committed to providing customers with comprehensive protection against viruses, spyware, and other new and existing malware. This organization is composed of a dedicated group of experienced analysts and Microsoft security technologists that are responsible for researching and responding to new threats, as well as providing the necessary security technology and infrastructure to protect customers.
The Microsoft Malware Protection Center supplies the core antimalware technology (including the scanning engine and malware definition updates) for Forefront™ Client
Security, Forefront Server Security, Windows® Live OneCare™, Windows Defender, and
other Microsoft security solutions and technologies.
Its global malware research system consists of ongoing security research based on feed back submitted by the worldwide users of Microsoft security products, combined with advanced automated analysis techniques, to help discover and respond to threats quickly. By analyzing information collected from sources worldwide, the research team is able to monitor trends on a global basis.
■
Understanding Anti-Malware Research and Response at Microsoft
Key Malware Trends
As part of its efforts, the Microsoft Malware Protection Center conducts ongoing research into malicious and potentially unwanted software to understand trends that can affect customers. The team publishes reports outlining key trends in the threat and software vulnerability landscape. The latest Microsoft Security Intelligence Report (for more infor mation, see the appendix) covers data from July to December 2006 and reveals several emerging trends:
Money as a Motivating Factor: Historically, many malware programs existed for the purpose of vandalism or ego gratification. The evolution of spyware and other potentially unwanted software highlights financial gain as a key incentive for the authors of this software. Instead of destroying data, spyware often tries to collect personal information or deliver advertisements for money.
Current malicious behavior can range from collecting commissions for installing potentially unwanted software to committing fraud using a user’s private financial information.
Targeted Malware Distribution: The nature of malware distribution has changed. In the past, worms like Blaster and Sasser spread quickly around the world, infecting millions of machines and catching the attention of the media and the general public.
Today, much of the new malware is a non-replicating Trojan, specifically designed to avoid the notice of consumers and security vendors. Malware authors are avoid ing overt signs of infection, such as crashes and a high volume of network traffic, and moving to more subtle symptoms, like data theft.
Increasingly Complex Threats: The techniques used to create malware have become more complex over time. Previously, malware authors may have mutated their creations in reaction to detection by security software. Today, malware authors may actively create thousands of variants ahead of time to get a head start on avoiding detection.
Malware authors are increasingly using tools, such as rootkits and packers, to make threats more difficult to detect and analyze. Likewise, malware authors increas ingly employ social engineering to trick the user into installing the software. Ongoing data analysis and investigation into the malware landscape is critical, because today’s threats are more advanced, occur more frequently, and are increasingly motivated by profit. By tracking key trends and emerging threats, the Microsoft Malware Protection Center is able to prioritize its work on protecting customers from the threats that are cur rently trying to exploit them (threats “in the wild”).
■
■
Understanding Anti-Malware Research and Response at Microsoft
Overview of the Microsoft Malware Protection Center
The Microsoft Malware Protection Center uses a research and response process through which it monitors submissions and reports from around the world, analyzes suspect malware, and delivers updates for the latest protection. Figure 1 shows a highlevel view of the Microsoft approach to antimalware research and response.
Figure 1: Overview of the Microsoft anti-malware response lifecycle
The Microsoft Malware Protection Center interacts with customers and the security industry in a multistage process. These stages and roles include:
Industry Collaboration: Security is a global concern. Whatever the customer’s choice of security provider, networked computers exist within an ecosystem where an infected machine can attack healthy ones, such as by sending thousands of spam messages or being used as part of a denialofservice attack. It is impor tant for industry players to share research knowledge to help move security pro tection forward.
To promote industry collaboration, Microsoft founded the Virus Information Alliance (VIA), was a founding member of the AntiSpyware Coalition (ASC), and is a premium member of the AntiPhishing Working Group, with the goal of collabo rating with industry partners in the fight against malware.
Global Observations: The first stage of the analysis process is to gather data on malware. This information can come from many channels, such as automated collection tools, product support, or industry sample sharing. However, a large amount of useful data is often submitted by customers, based on the issues that they’re seeing on a daytoday basis.
■
Understanding Anti-Malware Research and Response at Microsoft
Malware Research Analysis: The research team examines the tactics and tech niques currently used by malware, such as obfuscation. The information gathered from existing malware can be used to create additional definitions and guide future enhancements to the antimalware engine. For example, a researcher may notice that malware is taking advantage of a new obfuscation technique and he or she may suggest engine enhancements to counteract it.
Malware Response: The response team is concerned with quickly creating solutions to customer issues. The team combines incoming data with automated analysis techniques to respond quickly to current and emerging threats that affect our customers.
In the case of an outbreak, the response team would analyze incoming malware samples and create the appropriate engine definitions. The team can use the data gathered to create a queue of important items to investigate, based on realtime customer concerns.
Signature Definitions: After malware is analyzed, the final output is a malware
definition, the data used by the engine to identify and remove a threat. The defini tion may include patterns inside the malware, as well as cleanup and remediation steps necessary to restore an infected machine to its original state.
Testing: After the definition is created, it undergoes various testing passes to help ensure the signature behaves as expected. The Microsoft Malware Protection Center has collections of files against which the signature can be tested to help ensure it classifies threats correctly.
If a misclassification is found, the updates follow a roll-forward model. A revised definition is then created, tested, and published to supersede the previous one. In this way, customers do not lose protection against the other emerging threats in the definition file.
Definition updates can also include an update to the core anti-malware engine, which can provide enhancements to scanning, detection, and removal capabili ties. In these cases, the engine undergoes a rigorous testing process in addition to the standard definition tests.
Publishing: Once the definitions have been certified through testing, they are digitally signed and packaged for distribution. The digital signature guarantees the authenticity and integrity of the file, and the distribution packaging creates various full and partial updates for the client. Depending on how frequently a client updates, it may only need to install a small change to the definitions rather than a complete update.
■
■
■
■
Understanding Anti-Malware Research and Response at Microsoft
Definition updates are published by Microsoft multiple times a day. Administra tors can manage and deploy updates using their existing update framework and policies, such as by using Windows Software Update Services and Group Policy (for more information, see the Microsoft Forefront Client Security Web site in the appendix).
User Education: In addition, analysts may enter relevant information into the Malware Encyclopedia, providing customers with additional details about the nature of threats, side effects, and any specific remediation required. Although an analyst may add a single threat or threat family at a time, a particular defini tion release may contain the combined data for many malware programs. The customer is a critical part of the feedback loop for the research and response team. As customers install definitions and scan for malicious software, they can choose to send telemetry information and samples to the Microsoft Malware Protection Center for analysis. The active involvement of customers in the research and response process provides insight into current malware trends, enabling the Microsoft Malware Protection Center to respond quickly with updates to help protect customers.
Key Response Highlights
Several features characterize the Microsoft Malware Protection Center and global malware research system, as summarized in Figure 2.
Figure 2: Key characteristics of the Microsoft Malware Protection Center
Understanding Anti-Malware Research and Response at Microsoft
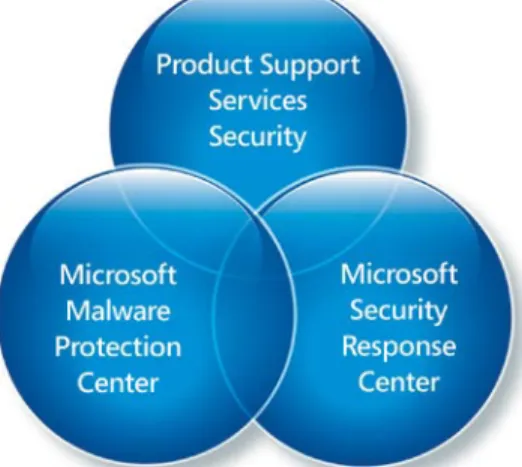
Figure 3: Relationship between groups that help protect customers from malware
Global Organization
The Microsoft Malware Protection Center includes not only experienced analysts previ ously at Symantec, McAfee, Computer Associates, FSecure, and other organizations, but also Microsoft engineering and technology specialists who understand best practices in increasing the security of the Microsoft platform, applications, and infrastructure. This team is headed by Vinny Gullotto, who brings more than a decade of experience in the antivirus industry. Gullotto was formerly Vice President in charge of McAfee’s Anti Virus Emergency Response Team (AVERT). His team includes, among others:
Jimmy Kuo, Senior Security Researcher. Kuo has more than 12 years of experience in virus research. He was previously a research fellow at McAfee’s AVERT Labs; a manager of Symantec’s NAV Lab; and held positions at IBM and Computer Associates. Kuo was the keynote speaker at AVAR 2000 and the Virus Bulletin Conference, was awarded the Fed 100 Award for his work on the Melissa virus, and served on the Presidential Y2K Council’s Information Coordi nation Center.
Katrin Tocheva, Microsoft European Lab Manager. Tocheva has more than 15 years of virus research experience. She has held previous positions at FSecure Corporation and the National Laboratory of Computer Virology in the Bulgarian Academy of Science. She is a member of CARO (Computer Antivirus Researchers’ Organization), AVAR (Association of anti Virus Asia Researchers), and a board member of AVED (AntiVirus Emergency Discussion Network). The team continues to expand its analyst coverage with sites in Europe, the Americas, and Asia for comprehensive 24/7 coverage. Because this organization is responsible for supporting multiple Microsoft security products and technologies—Forefront Client Security, Forefront Server Security, Windows Live OneCare, Windows Defender, and others—it benefits from the experience and expertise that comes from supporting and securing millions of computers worldwide. Customers can learn more about the activi ties of the Microsoft Malware Protection
Center in its public blog, which provides customers with ongoing updates to its research practices (for more information, see the appendix).
In addition, the Microsoft Malware Pro tection Center integrates with the Micro soft Security Response Center (MSRC) and Product Support Services Security (PSS Security) to share information and procedures about malware-specific issues (Figure 3):
■
Understanding Anti-Malware Research and Response at Microsoft
Microsoft Security Response Center (MSRC) is a leading industry organization provid ing vulnerability information to security providers. The Microsoft Malware Protection Center receives this information in the same manner as other security partners.
Because the Microsoft Malware Protection Center team understands the public MSRC process, it is able to ensure its processes are optimized to deliver prompt response to emerging issues. In addition, it is able to share information and procedures that are useful for research on existing malware.
For example, tools, efforts, and learning are coordinated when analyzing active malware that is using a known vulnerability, leading to improved detection rates and additional information about the vulnerability. This allows for a more complete and rigorous analy sis of the malware, and enhanced detection and removal for customers.
Since its introduction in 1996, the MSRC has been effective in providing security infor mation has and won industry acclaim in its response to malwarerelated incidents. Over time it has continually improved how Microsoft responds to security incidents with cus tomers. Key initiatives and best practices, such as the Security Development Lifecycle (SDL) process, continue to bolster the security process throughout Microsoft.
Product Support Services Security (PSS Security), the Microsoft support organization, has extensive experience in supporting customers facing malwarerelated issues. As an organization, PSS Security has the flexibility and depth to deal with malware incidents in a Windows environment, as well as the knowledge to deploy solutions that integrate with Software Restriction Policy, Group Policy, and other Microsoft technologies. In addition, PSS Security will provide support for Forefront Client Security, guiding enterprises to take advantage of its capabilities.
The Microsoft Malware Protection Center shares an integrated process with PSS Security, through which Forefront Client Security customers can submit malware to Microsoft for analysis in a streamlined manner. First, customers can submit suspected files directly to the Microsoft response team through a content portal, which is described later in this doc ument. Analysts are notified of the incoming submission, and preliminary determination on the file is sent back to the customer. After the analyst makes a final determination, the results are sent back to the customer, along with supplementary information to help the enterprise deploy updated definitions if they decide to take that course of action.
For malware submissions that need the highest priority response, Forefront Client Security customers can contact PSS Security directly and work with a support representative to analyze the file. The PSS engineer can submit the file on behalf of the Forefront Client Security customer, and provide a central point of contact for definition-related issues and priority resolution.
Understanding Anti-Malware Research and Response at Microsoft
While sample collection from Windows Defender and Microsoft Windows Live OneCare is typically used for general analysis and trending purposes, data received from Forefront Client Security customers is highly prioritized and receives an individual response. The collaboration between the Microsoft Malware Protection Center and PSS Security ensures that enterprise customers receive the highest level of response to malwarerelated security incidents.
Advanced Telemetry
The Microsoft Malware Protection Center maintains a global perspective on malware trends through an analysis of the feedback collected from a variety of sources. These sources include released products and technologies, such as Microsoft Forefront Client Security, Microsoft Forefront Server Security, the Malicious Software Removal Tool (MSRT), Windows Live OneCare, Hotmail®, Microsoft Exchange Hosted Services, and
other Microsoft protection technologies, as well as internal sources, such as our PSS Security support organization and other datagathering tools.
Microsoft partners with external industry organizations, such as VirusTotal, AVTest.org, KISA, and VIA, to share information and trends. In addition, Microsoft publicly provides information about its findings on emerging malware trends through publications, such as the Microsoft Security Intelligence Report.
As malware becomes increasingly transient in attempts to evade detection, it is important to have critical insight into the daily and hourly patterns of behavior, and to prioritize work appropriately. By using multiple data sources, we are able to get a comprehensive perspective on the malware landscape and identify emerging threats.
For example, the Microsoft Windows Malicious Software Removal Tool (MSRT) is designed to help identify and remove specifically targeted, prevalent malware from customer computers, and is available at no charge to licensed Windows users. Since its initial release in January 2005, its user base has grown to 310 million unique computers
which have executed the tool more than 5.5 billion times. The MSRT is just one of the sources of threat telemetry used by the Microsoft Malware Protection Center, and it has also been an effective tool for removing malicious software from computers around the world. For 75 percent of the 12 malware families that are part of the tool, the number of computers that required clean ing decreased by a range of 33 to 70 percent from the first half of 2006 (1H06) to the second half (2H06).
The Windows Defender voting network (otherwise known as SpyNet) provides another example of how Microsoft researchers can gather advanced insight into emerging threats. Users of Windows Defender can choose to participate in a worldwide network of users that help discover and report new threats.
“
As malware becomes increasingly
transient in attempts to evade
detection, it is important to have
critical insight into the daily and
hourly patterns of behavior, and to
Understanding Anti-Malware Research and Response at Microsoft
Customers who choose to participate in SpyNet can respond to requests for malware sam ples from the research team, as well as submit generically detected suspicious files. Users of Windows Defender alone identified and reported on over 38 million pieces of poten tially unwanted software in the second half of 2006. Similarly, customers of Windows Live OneCare can also choose to share information with Microsoft on the types of threats being detected on their machine. This customerdriven telemetry from both Windows Defender and Windows Live OneCare helps analysts focus on the most prevalent issues. These and other technologies allow analysts to correlate and recognize patterns in behav ior across a broad range of customers. For example, if a Trojan is released on a small scale to avoid detection, this analysis of trends can detect a spike in suspicious behavior, even if it only affects hundreds or thousands of clients. Analysts can notice the increase and investigate the potential malware before it becomes widespread.
Rapid Response
The team performs rigorous analysis on collected data through a combination of automa tion, security expertise, and testing processes to identify the latest malware threats. This approach involves significant investment in automation to effi
ciently use analyst resources and deliver rapid response. An example of this automation involves the handling of malware submissions. The systems in place perform automatic malware submission stor age and retrieval, resolving of duplicate submissions, grouping of submissions, and prioritization of sample analysis to reduce analy sis time.
Ongoing research into behavioral classification allows analysts to automatically group malware into related families based on
similar characteristics. This is especially relevant given that malware authors are releas ing numerous variations of the same program to avoid detection. In addition, a pluggable infrastructure allows for reduction of manual steps and ease of insertion of additional sample data.
Together, these capabilities assist in automating the process of analyzing malware activity, including its associated effect on files, the registry, and network events. By automating repetitive tasks and quickly analyzing large data sets, the response team is able to quickly identify malware and deliver signatures to customers.
In addition to delivering rapid response through signatures, the analysts also use the capabilities of the Microsoft AntiMalware Engine to perform advanced removal tech niques, such as reverting specific side effects (like changed settings) to clean an infected machine.
“
The team performs rigorous
analysis on collected data through a
combination of automation, security
expertise, and testing processes to
identify the latest malware threats.
”
Understanding Anti-Malware Research and Response at Microsoft
0
Dynamic Translation, another area of research, allows the antimalware engine to generi cally decrypt malware that has tried to scramble its contents. Automated decryption techniques tend to be complete but very timeintensive, while
manually created routines are fast but require sig nificant effort to maintain (which does not scale given the increasing number of malware variants). Dynamic Translation provides both speed and cover age by optimizing how the malware’s instructions are analyzed, allowing for the fast, generic decryp tion of malware. In addition, Dynamic Translation can be extended to areas such as behaviorbased analysis of malware samples.
Microsoft delivers guidance to customers through an integrated communications approach with PSS Security to respond quickly to customer issues and provide actionable customer guidance. The Microsoft Malware
Protection Center web portal, released in April 2007, delivers uptodate information about current threats, news, and research from the Microsoft Malware Protection Center. Customers can get key insights on the top threats to their environments and review specific details through a searchable malware encyclopedia. Customers are also able to submit malware samples for analysis through this portal, with Forefront Client Security customers receiving prioritized response.
Forward Strategy and Vision
Microsoft’s vision is to be one of the leading global malware research organizations, delivering accurate and timely updates to our customers consistently and reliably. The Microsoft Malware Protection Center is focused on delivering worldclass security response with a commitment to quality, timeliness, and accuracy in addressing threats that affect customers.
Near-Term Strategy
In the near term, the Microsoft Malware Protection Center will deliver malware support consistent with other leading malware research organizations. Among other areas, this includes:
Definition Quality and Coverage: Delivers detection rates to customers, com parable to industry leaders, across all aspects of a threat. The Microsoft research team is committed to working with testing organizations to understand the methodology used for comparisons, and to continue to focus on the current “inthewild” issues facing customers today, be they viruses, worms, or Trojans. ■
Figure 4: The Microsoft
Understanding Anti-Malware Research and Response at Microsoft
Anti-Malware Response Time: The Microsoft response team will work to deliver response and update times that meet or exceed customers’ expectations in light of the rapidly changing threat landscape. The team’s target is to respond and make definitions available to customers within hours of identifying a high-priority threat, while providing enterprises with premium support, as described earlier.
Future Vision
In addition to these nearterm plans, the research and response team is anticipating future trends and customer needs to provide nextgeneration protection.
Coverage of the Threat Event: Currently, industry tools focus on the end result of a malware infection: the files and programs installed on a customer’s machine. For more complete analysis and forecasting, investigation of the entire chain of events leading to infection can give insights and warnings about future malware activity. For example, a spam email may contain a link to a phishing URL, which downloads a selfupdating Trojan.
By examining multiple data sources and the gateways that threats use to propagate, the research and response team can identify and respond to patterns of activity that are beyond the specific details of one installation. Over the long-term, the Microsoft Malware Protection Center envisions the delivery of integrated, simul taneous response to threat events that cover multiple response channels.
Anticipating Future Trends: The malware landscape has changed enormously over the past decade, but it has changed even more dramatically in just the past few years. If the past is an indication of the future, new threats will emerge as technology and incentives evolve, just as spyware, phishing, and other financially motivated attacks reflect the current goals of today’s malware authors. Microsoft researchers are continuously monitoring emerging trends and potential infection vectors to stay abreast of future potential attacks.
Continuing Industry Participation: Security is an industrywide problem and requires industrywide solutions. In this networked world, customers exist and communicate in the same ecosystem and need protection from malware threats. As threats become increasingly complex, it is important for the security industry to collaborate in protecting users.
Forums such as the Microsoft Virus Initiative (MVI), the Virus Information Alliance (VIA), and the AntiSpyware Coalition (ASC) provide the means for security vendors to share tools, information, and best practices in the fight against malware. As a founding member of these organizations, Microsoft is committed to providing customers with choice in terms of antimalware coverage.
■
■
■
Understanding Anti-Malware Research and Response at Microsoft
Concluding Thoughts
The current malware landscape is changing quickly. Threats continue to evolve, becom ing more advanced and more motivated by financial gain. At the same time, consumers and enterprises operate in a highly networked environment. Microsoft is committed to help protect customers from current and emerging malware threats, while fostering industry collaboration for the benefit of the computing ecosystem.
Through an experienced team, combined with advanced telemetry, automation, and integrated processes, the Microsoft Malware Protection Center will deliver global research and response in a reliable, accurate, efficient, and consistent manner to address the needs of its customers.
Appendix: Related Resources
Additional security information about the role of the Microsoft Malware Protection Center and malware protection can be found in the following resources.
Websites
Microsoft Malware Protection Center Portal: This site provides customers information on the latest malware threats and trends.
http://www.microsoft.com/security/portal
Forefront Client Security: This site includes information about Microsoft Forefront Client Security, an antivirus and antispyware solution for protecting business desktops, laptops, and server operating systems.
http://www.microsoft.com/clientsecurity
Anti-Malware Team Blog: This site contains ongoing reports and research papers on the latest malware trends.
http://blogs.technet.com/antimalware/
Reports and White Papers
Microsoft Security Intelligence Report: July-December 2006 http://www.microsoft.com/technet/Security/default.mspx (The previous version of the report is available at: http://go.microsoft.com/?linkid=6543860)
Understanding Anti-Malware Technologies
http://www.microsoft.com/forefront/whitepapers/default.mspx
Unified Protection for Clients
http://www.microsoft.com/secureclient/default.mspx
Defeating Polymorphism: Beyond Emulation
http://microsoft.com/downloads Behavioral Classification http://microsoft.com/downloads ■ ■ ■ ■ ■ ■ ■ ■