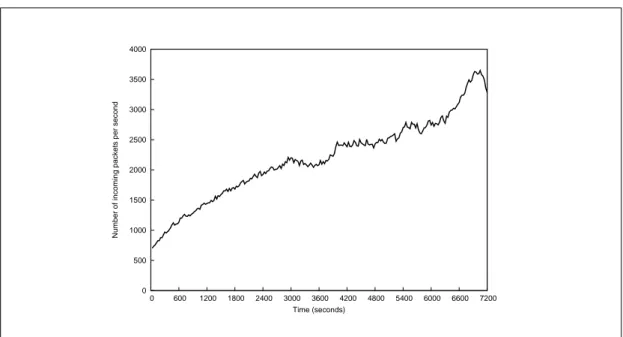
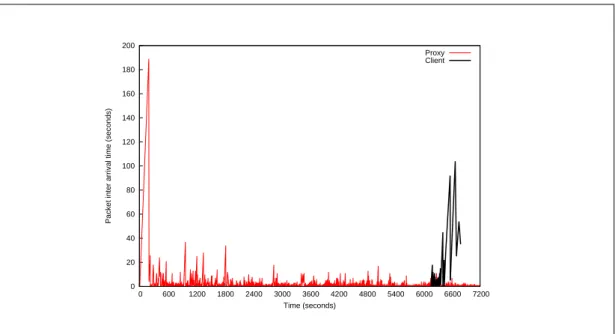
Detecting distributed Denial-of-Service attacks and Flash Events
Full text
Figure
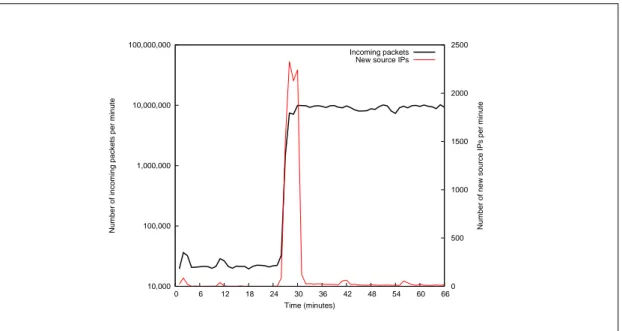


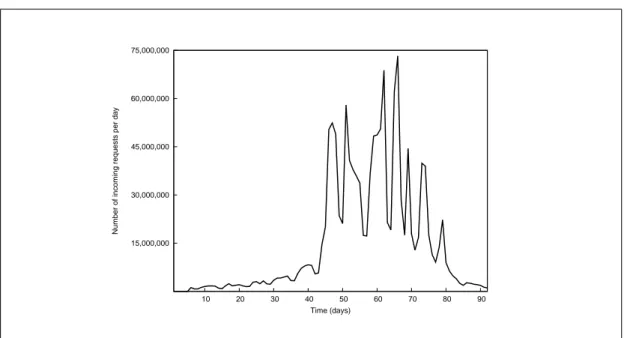
Related documents
Federalni komite za geografske podatke (Federal Geographic Data Committee, FGDC) je vladni komite ZDA, ustanovljen leta 1990, z nalogo, da koordinira uporabo geoprostorskih podatkov
calibration, correct any errors, re-run GPROF and observe any differences.
In this thesis, we extend Hongning Wang’s work [1] of solving Latent As- pect Rating Analysis problem. We compute restaurants aspect rating by aggregating aspect rating of reviews
campus transition with more ease to university life, graduate faster, and are more involved with the university than students who live off campus.. How to pay
Pereg et al conducted the randomized blinding controlled trial in 2011 to study the effect of probiotics on clinical and laboratory parameters of patients with compensated
3,13 Results of this study has revealed that neovascularization was meaningfully decreased in groups treated by topical and subconjunctival diclofenac compared with control
December 17, 2010 Stefan Niemann, University of Essex: Channels of Firm Adjustment: Theory and Empirical Evidence December 1, 2010 Lucrezia Reichlin (London Business
With Google Analytics as the given web analytics package of Fonq we decided to push a custom variable to Google Analytics filled with the fact if the internal search user