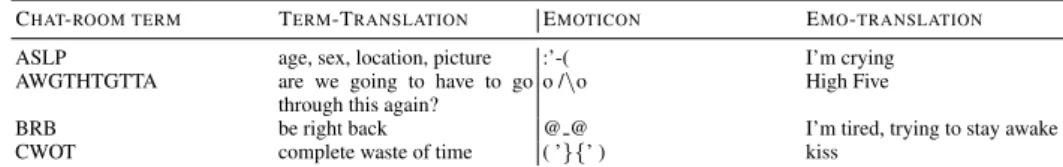
Detecting child grooming behaviour patterns on social media
Full text
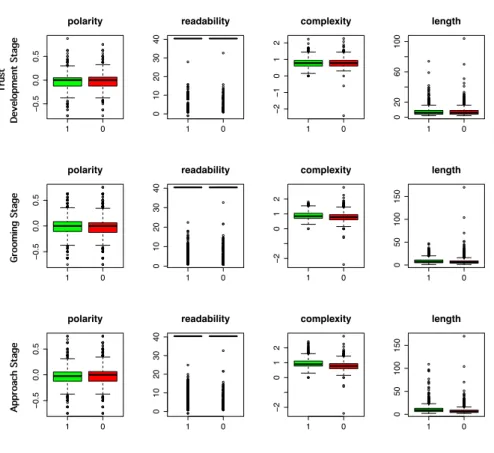
Figure
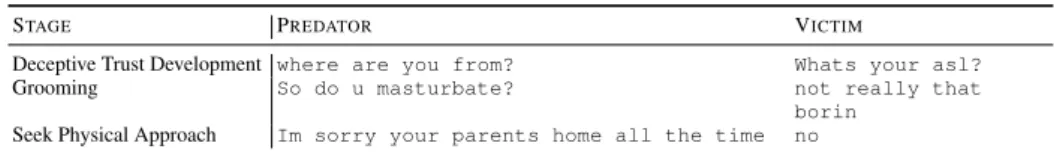
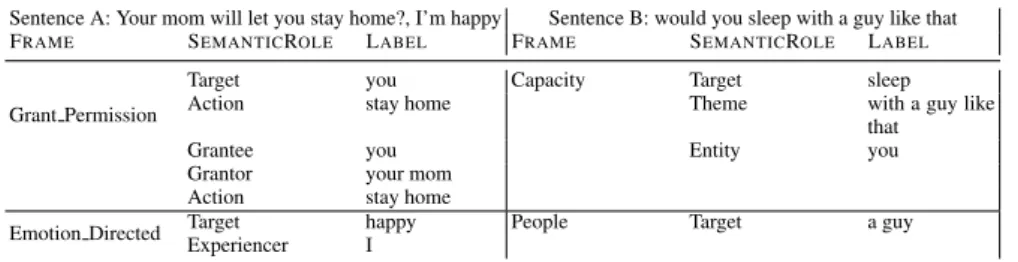
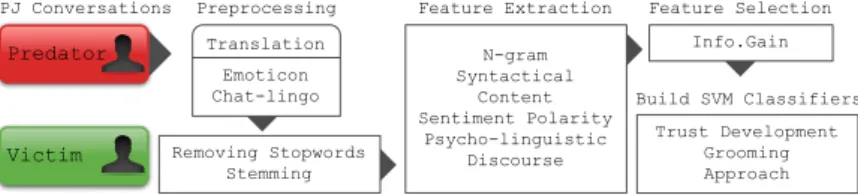
Related documents
• M1: tokens are independent, identically distributed, have uniform probability. • M2: tokens are independent, identically distributed, have
Consider, for instance, the situation where there is a change of legislation in some year t and one expects that the incremental claim payments X i , j in future calendar years i +
First, we estimate an aggregated hedonic equation with monthly time dummy vari- ables, and compare this index with arithmetic mean and median price indexes.. Although the three
Rated current is available across the entire drive full power range Drive operating range = † Lowest nominal motor voltage - 10% to drive rated voltage + 10%. Drive output is
of the effects of dynamic strength training on muscle strength activity, functional capacity and bone mineral density in early rheumatoid arthritis. Komatireddy G, Leitch R, Cella
The hydraulic system delivers the active ingredient to the point of injection, which was placed at the boom (T-configuration, Fig. 3 I.) and at the nozzle (straight
Puji syukur kepada Tuhan Yesus atas kasih dan anugerahnya sehingga penulis dapat menyelesaikan skripsi dengan judul “PENGARUH FINANCIAL DISTRESS, DIVIDEND PAYOUT
The opportunities emerging from focusing on the accreditation of diagnostic services were to enable joined up working and collaboration across patient care pathways to create