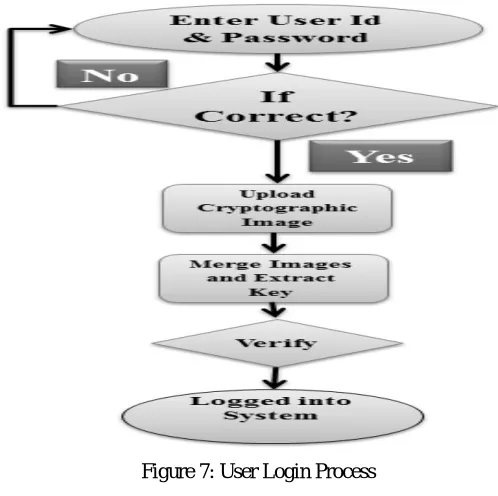
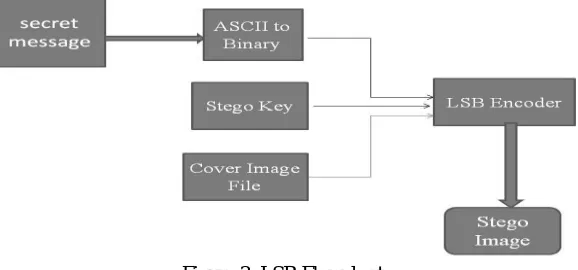
A Hybrid Data Hiding Approach for Securing Online Transactions
Full text
Figure


Related documents
Step 2: Select File Claims in the Accounts tab and select the plan for which you would like to file a claim.. Step 3: Select the File Claim button from the plan you would like
Step 2: From the View Wires for drop-down menu select the account wire is for. Step 3:
Step 1: Complete Your Billing and Shipping Information Step 2: Select a Shipping Method and a Payment Method Step 3: Review and Submit Order.. Step 4:
Although Japanese civil society showed social resilience, solidarity, and coherence in response to the earthquake and tsunami devastation, Japan as a whole failed
ing of what at the time was called ethereal energy (energy that was supposed to come from the ether). Those alchemists knew about the forces of nature in as much as their
sinapina transcriptome with KEGG revealed a number of gene transcripts differently regulated in the presence of betulin including 23 transcripts encoding enzymes involved in
Step 3: When the Insert Function dialog box appears Select Statistical in the Or select a category box Select COUNTIF in the Select a function box Click OK. Step 4: When the
STRATEGY FOR TESTING, COHORTING, PERSONAL PROTECTIVE EQUIPMENT, AND STAFFING To ensure the facility has taken appropriate measures to protect residents and staff, descriptions of