Evaluation of DHS' Information Security Program for Fiscal Year 2015
Full text
Figure
Related documents
The optimally integrated benefit design differs from the standard single good designs by taking into account cross-price elasticities between the several services and goods
Bu tercihlerinin kendilerine nasıl davranıldığıyla değil, bu insanın yi yeceğini başka maymunlarla paylaşarak edindiği şöhretle alakası vardır.24 Bizim kendi
We expect the ongoing reduction in vacant space to sustain rental growth for the rest of the year in the German cities.. In Milan, the current state of the market and the ongoing
Based on management’s response and our review of information provided by the Office of Information Technology, we deleted one recommendation (draft report Recommendation 3) that
Furthermore, this chapter presents the role of attachment theory, parental practices, how the marital status, socio-economic status and gender of the parent could
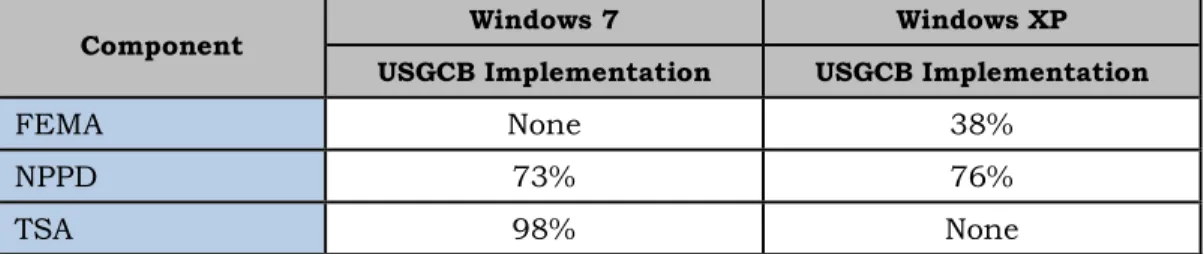
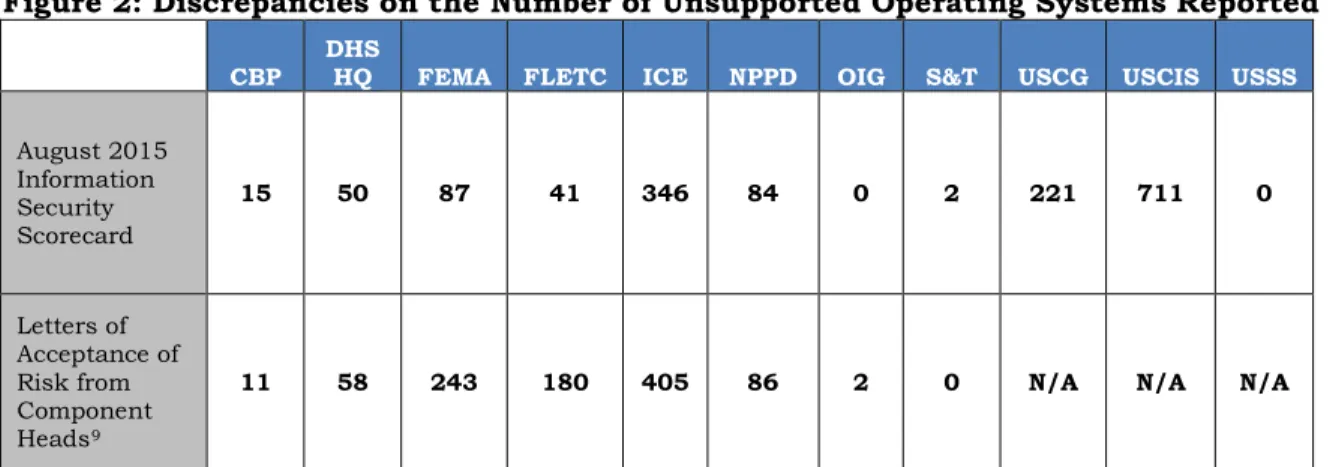
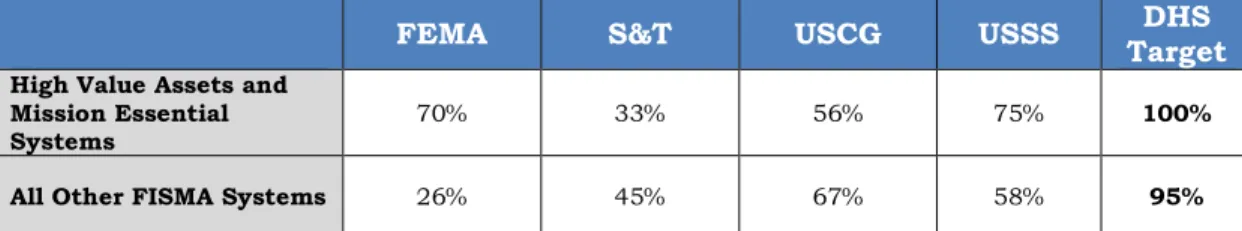
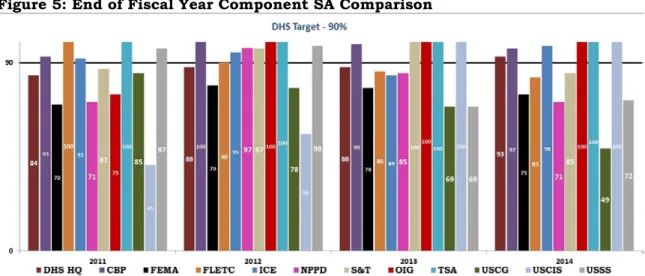
As part of our Technical Security Evaluation Program, we evaluated technical and information security policies and procedures of Department of Homeland Security components at
Specifically, we: (1) used last year's FISMA evaluation as a baseline for this year's evaluation; (2) reviewed policies, procedures, and practices that DHS had implemented at
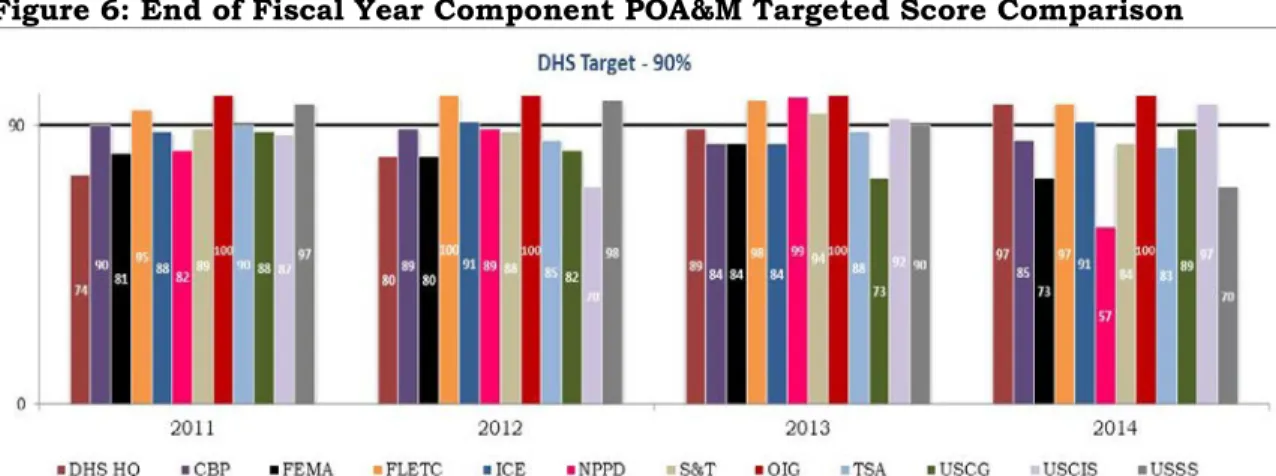
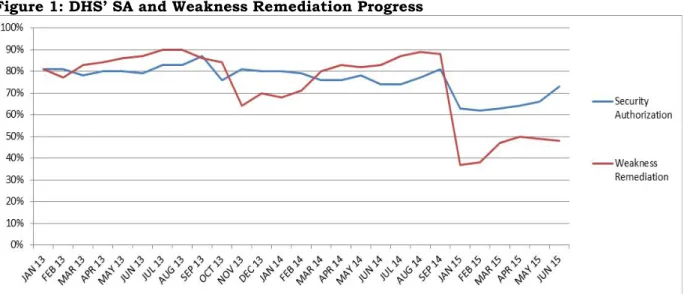
Component levels; (3) reviewed DHS’ POA&M process to ensure that all security weaknesses are identified, tracked, and addressed; (4) reviewed the processes and status of