OVERCOME PASSWORD HACKING THROUGH GRAPHICAL PASSWORD AUTHENTICATION
Full text
Figure

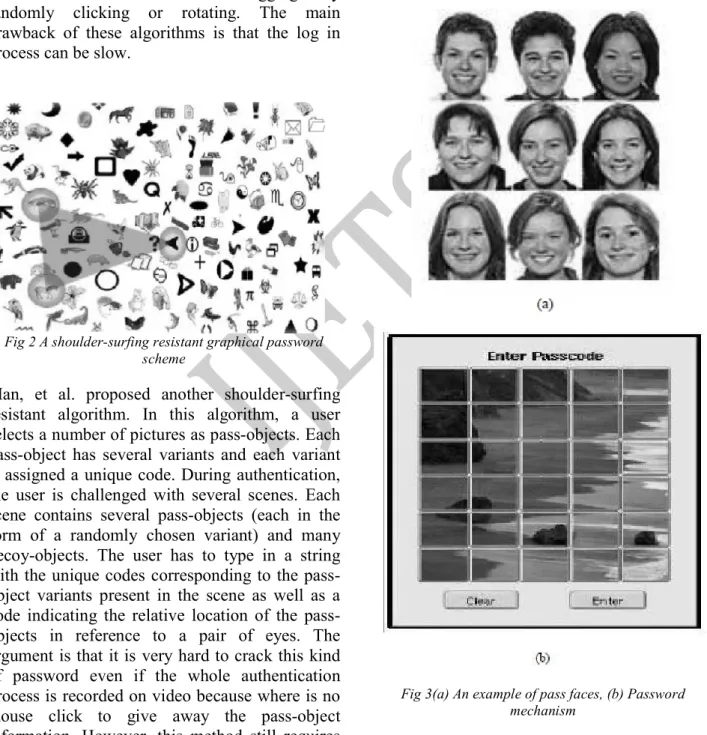
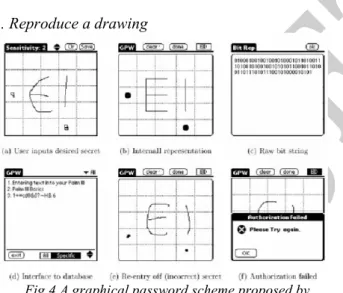
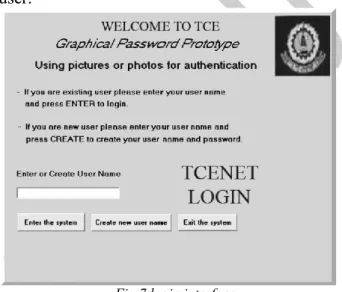
Related documents
Table 4.14: Total number of sentences in the 2011 DDI Extraction challenge corpus eligible as training and test instances for sentence filtering using negation scopes..
The handbook complemented the video (Table 1) and summarized findings from scientific studies about differ- ences in patient-reported and clinical outcomes among patients
These publications refer to 372 individual allergenic and 184 irritant agents or worksites that were identified to cause occupational asthma, of which 36 were listed as both
We report about a female patient suffering from schizophrenia with drug-resistant obsessive musical hallucinations.. The patient volunteered in a nine months pilot study to follow
We invite unpublished novel, original, empirical and high quality research work pertaining to recent developments & practices in the area of Computer, Business, Finance,
The variation i n the frequency with which different rll-diploids produce r- segregants and in the ratio with which the two types of r-segregants are produced indicates
In addition, Musundi (2014) opine that financial literacy influences investment decision making because individuals with low literacy often rely on others as
Lane 1, amido black-stained blot of BCSP; lane 2, immunoblot incubated with positive control serum from an experimen- tally infected cow (cow 47); lane 3, immunoblot with a