Design and Implementation Guide. Data Center Design Guide: Implement McAfee Next Generation Firewall for the Perimeter
Full text
Figure

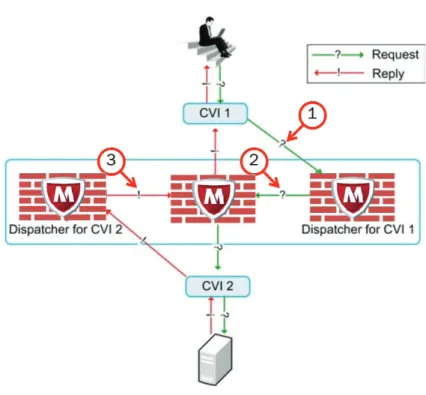
Related documents
The new exponential-related func- tion (ER), which has been developed and adopted in the intuitionistic fuzzy TOPSIS model and intuitionistic fuzzy entropy is used for solving
Therefore, the attenuation of the patch cord and backbone cable, associated connector insertion loss, and the insertion loss value of the cassettes should not exceed the
Acknowledging the lack of empirical research on design rights, our paper wishes to investigate the risk of piracy and the perceptions of the registered and unregistered design
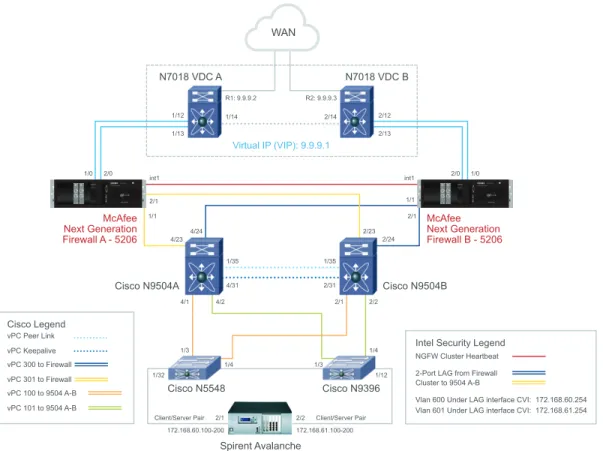
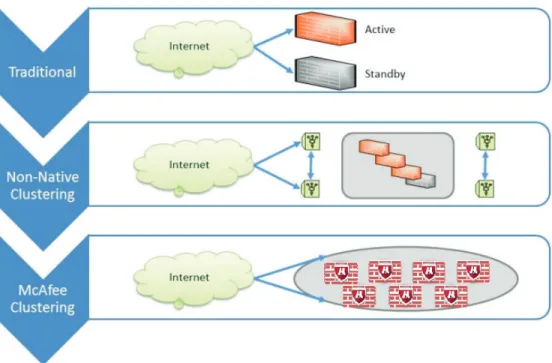
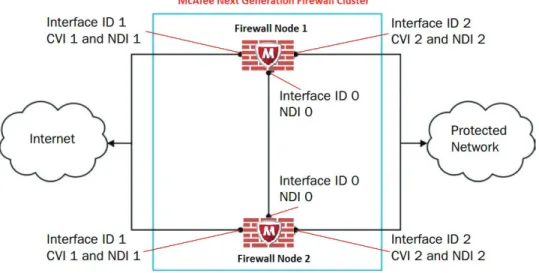
McAfee Next Generation Firewall and McAfee Security Management Center offer an optimal solution for enterprises, as they meet the needs of both network/network operations and
Secure workloads: McAfee offers a holistic approach: • Host-level ° Secure against fast-changing threats with dynamic whitelisting and blacklisting antivirus °
A Xirrus wireless network simplifies and speeds the deployment of Raritan environmental sensors and intelligent power monitoring, including cost benefits realized through deploying
Complex-valued wavelet artificial neural network used Mexican hat wavelet and Haar wavelet function as hidden layer AF instead of logarithmic sigmoid activation function.In this
The Materials are subject to change without notice and do not represent a commitment on the part of Realtime Publishers, Inc or its web site sponsors.. In no event shall