Vol 4, No 1 (2018)
Full text
Figure




Related documents
The value shown is the market value that has
Building upon the insights of the identified BMI frameworks and elements, we derived six important components of a BMI framework: environmental BMI dimensions, central
During the research it was determined that expectations of all nine quality criteria of lower loyalty stage customers (neutral and potentially loyal) were higher than of higher
V drugi hipotezi trdimo, da rešitev Social CRM ponudnika Microsoft najbolje pokriva vse module rešitve CRM ter izkoristi vse bistvene funkcionalnosti družabnih omrežij, v primerjavi
However, qPCR on p53-ChIP material from a neuroblastoma cell line with wüd-type p53 (MYCN3) treated with nuüin-3 could not confirm direct bindüig of p53 to MIR182, MIR203, MIR222,
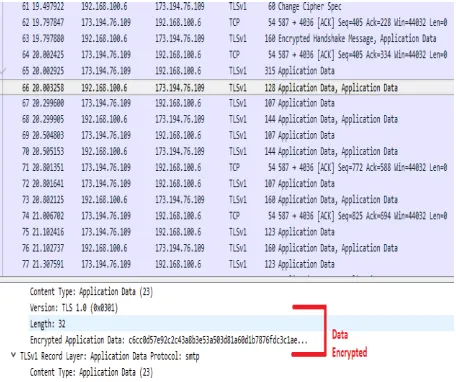
Direct Implementation HISP as an Endpoint Direct (SMTP / SMIME) Sending HISP E-Mail Server Security/Trust Agent SSL/TLS Receiving HISP E-Mail Server Security/Trust Agent
This document articulates requirements to vendors who produce software for Enterprises and Service Providers for Secure E- mail solution elements: E-mail Client, E-mail Gateway,
“This new COVID-19 antigen test is an important addition to available tests because the results can be read in minutes , right off the testing card.. This means people will know