Access control technologies for Big Data management systems: literature review and future trends
Full text
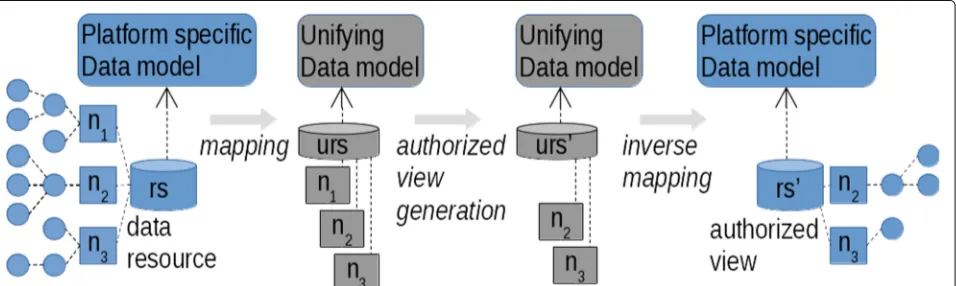
Figure


Related documents
estimates measure the impact of the experiment of changing the budget set of an individual- with mean net wage, virtual income and other characteristics- from pre-TRA1986
First, we evaluate the per- formance of SSDD by comparing the calculated semantic similarities with human ratings as described in [38] ; we then compare SSDD with other existing
• The instrument: while mobile financial services may provide access to existing sources of funds that are already regulated, such as bank accounts, mobile financial services may
In general, puzzle design can be thought of as a shape optimization problem – compute the best set of geometric pieces that can satisfy the given geometric constraints.. I will
The DADR model posits that specific social, cognitive, and behavioral factors related to the homework task (e.g., per- ceived difficulty and relevance of the task), provider
This property of SHMM1 was exploited for clustering cultivars (Cornelius et al., 1993) and for clustering sites (Cornelius et al., 1992; Crossa et al., 1993) into
The signi fi cant impact of gestational age at birth and delivery mode on gut microbiota progression is evident in the fi rst four years of life, while no mea- surable effects