Efficient Traceable Authorization Search System for Secure Cloud Storage
Full text
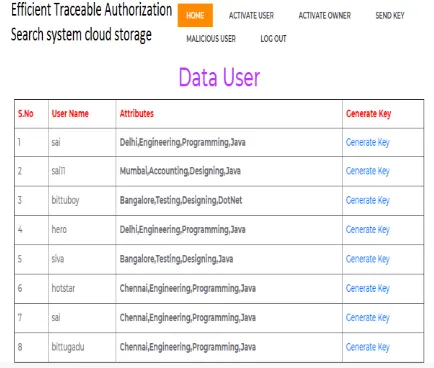
Figure

Related documents
[30] reported gross and histological lesions in IFN- γ R - mice but not in three wild-type mice strains (ICR, BALB/c and C57BL/6). A more recent study showed mild histological
9 shows the effect of EAACK protocol in the attack effected network and GERAF with EAACK in presence of attackers And the Ideal Network in terms of Packet
On 45° panel top face was punctured fully and core failure was observed shown in Fig6.At 30 J impact energy level the two peak loads were observed in the 45° stitched panel shown
Infrared thermography of dissipation caused by slippage of steel reinforcements embedded in the concrete matrix (temperature changes are given in degrees Celsius).. 3.5
The chuck cylinder is one of the most important components in the automated hacksaw machine because it is responsible for holding the work-piece firmly so as
The steady shear experiments was performed at 100 ⁰ C for both the ar-and c-PCL melts (Figure 20) and it was found that the c-PCL showed rapid shear thinning from a much higher
River during the spring of 2010 based on the linear spatial capture-recapture model (estimated individual activity centers) and observations (overall = sum of rkm / count of
Der knockout wurde durch Kreuzung einer unter dem Einfluß des pankreasspezifischen Ptf1a-Promotors stehenden Cre-transgenen Mauslinie mit einer von loxP-Sequenzen flankierten