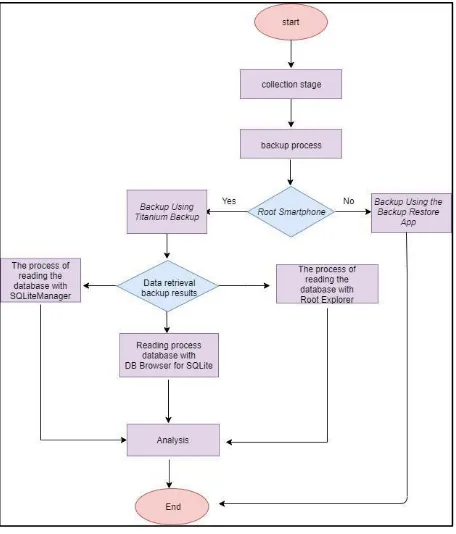
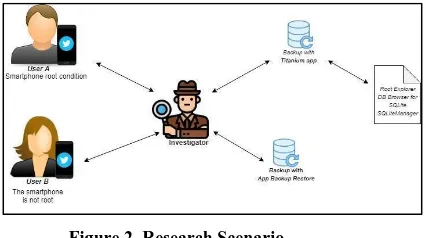
Analysis Mobile Forensics on Twitter Application using the National Institute of Justice (NIJ) Method
Full text
Figure


Related documents
122 | P a g e concepts (X=2.84); adapting teaching methods to meet indiv iduals student’s needs (X=2.74); linking students’ ideas, values and beliefs to their classroom
The single variable beam theories taking into account effect of transverse shear deformation for the buckling, bending and free vibration analysis of the thick beam
The name of the GroupServer configuration file (default INSTANCE_HOME /etc/gsconfig.ini ) that con- tains the token that will be used to authenticate the script when it tries to add
The tighter market climate, over-capacity, the weak develop- ment of business class travel and a rise in the lower yield long-haul traffic contributed to a fall in unit revenues
When more applications are received than there are places available, the following criteria will be used to decide which pupils are offered a place at an Islington community
Based on the three pillars of sustainability, environmental, social and economic, the aim of this report is to stimulate debate in Aotearoa New Zealand, amongst researchers
During Manager Self-Service (MSS) training in May and June, you will learn more about the access provided to Salary and Non-Salary Managers.. Q: Why is management getting access to
3 Prospect Theory and its relationship to accounting principles 3.1 The neoclassical roots of the current standards 3.2 Prospect Theory and the Balance-Sheet Approach 3.3 The