Data Security in Cloud Computing using Encryption and Steganography
Full text
Figure
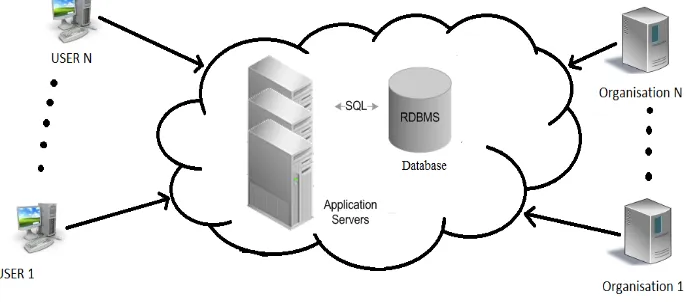

Related documents
6.1 Capacity for promoting community awareness of landscape benefits using virtual
Al-Hazemi (2000) suggested that vocabulary is more vulnerable to attrition than grammar in advanced L2 learners who had acquired the language in a natural setting and similar
Practically, we provide insight to practitioners, industry associations and policy/support bodies with regards to consumers ’ interpretations of the term ‘ craft ’ , and
The deviation of clustering coefficient C of the graph from the overall mean of the four groups as a function threshold T at three frequency bands..
En efecto, así como los libertarianos ven en cual- quier forma de intervención del Estado una fuente inevitable de interferencias arbitrarias –con la excepción de aquella acción
Proprietary Schools are referred to as those classified nonpublic, which sell or offer for sale mostly post- secondary instruction which leads to an occupation..
The constructs of entrepreneurial orientation, franchise paradox, service profit chain, rela- tionship marketing, best practice and service quality are now combined towards
When participants read the story in which the waiter used self-control, taking the waiter’s perspective led to generating fewer words than did not engaging in perspective taking,