SoK: Computer-Aided Cryptography
Full text
Figure
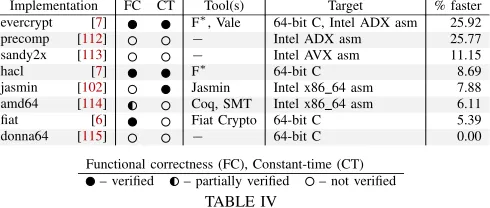

Related documents
The author uses standardised beta coefficients for all analyses because they are directly comparable and, hence, can give better insight into the relative contribution of
Applying Cox’s methodology, the Partnership calculated housing affordability in the nation’s 20 most populous metro areas using median house- hold income data from the ACS
The owner of your business (judge) wants you to suggest new customer service and public relations strategies to bring more business to the service station.. Your suggestions should
The relative thermal stability of the composite in comparison with the copolymer was proved via thermogravimetric analysis These results indicate the synergistic
- Taken from Project Delivery Options Volume 2 of 2 , by Georgia State Financing and Investment
Corresponding with the rising nutrient-level, chlorophyU-a and pH show a positive trend.. Salinity decreased
dimensjonene er emosjonell, informativ, instrumentell og evaluerende sosial støtte, Av disse vil jeg fokusere mest på den emosjonelle dimensjonen, slik House (ibid.) også gjør..
Encounter ✦ healing, Martial Standard Action Melee touch Target: You or one adjacent ally. Effect: The target can spend a