Integration of Data Confidentiality in Cloud Computing
Full text
Figure
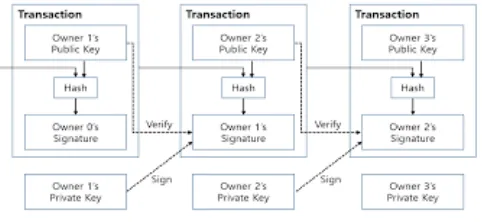
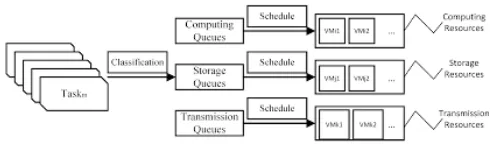
Related documents
Phylogenetic Diversity of Vibrio cholerae Associated with Endemic Cholera in Mexico from 1991 to 2008.. Seon Young Choi, a,b
156 Therefore, the Fifth Circuit declined to follow its earlier decisions holding that "prejudice is required in all occurrence policies, but that insurers need
10 6 Both the district court and the Federal Circuit held that patent exhaustion did not apply to method claims; 10 7 however, the Solicitor General cited several
To determine the ability of HIV-1 to inhibit the assembly of Se-induced SGs, U2OS cells stably expressing GFP-G3BP1 were transfected with Flag or Flag-Gag and exposed to Ars or Se..
The opinion had a good discussion of the rules that apply when one partner withdraws from a two-person partnership: (i) the withdrawing partner's only right was
Mercuric resistance genes were present in high abundance in both the contaminated- and background groundwater metagenomes across a wide phylogenetic breadth, and multiple
Cro2 mutant shows high levels of resistance to cephalosporins despite barely detectable levels of Stk on Western blot analysis suggests that the absence of StpA is the
clause was to operate. 94 Consequently, the court ruled that the indemnity provision was not conspicuous as required by the Texas Supreme Court. 9 5 Since the