Secure Authentication of Distributed Networks by Single Sign-On Mechanism
Full text
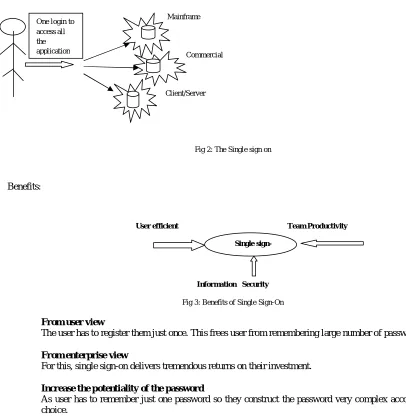
Figure


Related documents
Designing and Implementing Brand Marketing Programs 58 Measuring and Interpreting Brand Performance 60 Growing and Sustaining Brand Equity 60?.
If you are concerned about making your second session as passionate as your first, remember that it’s important not to compare each sexual experience, especially if doing so
The first section of this paper examines the background of Internet use for direct marketing, including the demographics of Internet users, elements of Internet marketing sites,
Use the Resprep® sample delivery system to transfer large volumes of low viscosity samples directly from a bottle to a solid phase extraction cartridge, or to a disk on a
From “gentlemen” and “heroes” to “real men” and “disabled men,” this article identifies dominant historical and contemporary images of masculinity and
the tax on real rather than nominal interest income, tax payments fall relative to what was reported in Tables 3 4, since dividend and capital gains income has dropped for all
(b) the termination of the Concession Agreement prior to the occurrence of the GOL Completion Date for the failure by the Company to achieve the GOL Project Completion Date due to