ENHANCEMENT OF SECURITY IN CLOUD COMPUTING USING STEGANOGRAPHY
Full text
Figure

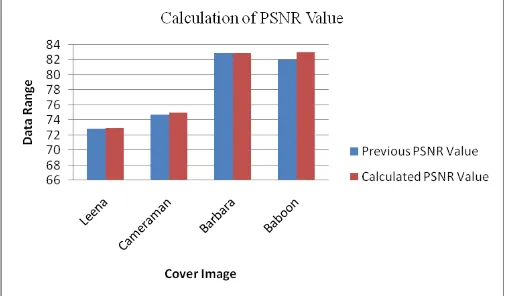
Related documents
Figure 8 clearly shows that news shocks have greater effects on economic activity variables (consumption, investment, hours, and output) if we remove uncertainty ef- fects from the
From table 3 we observe that using dedicated path-based protection scheme in network topology A, the total number of protection paths is 6, total working capacity
The deviation of clustering coefficient C of the graph from the overall mean of the four groups as a function threshold T at three frequency bands..
As more and more dental composites with different properties and qualities enter the clinics, this study was aimed to experiment the polymerisation shrinkage stress and
An analysis of the economic contribution of the software industry examined the effect of software activity on the Lebanese economy by measuring it in terms of output and value
We consider a discrete version of this problem in which competing suppliers each choose a reservation price and an execution price for blocks of capacity, and the buyer, facing a
Key words: agriculture, grain and products of its processing, competitiveness, prices, production volumes, export, import, price competitiveness factor, integral
Thermax enables Excel to be used as a modelling platform for conducting parametric and optimisation analyses of power generation and refrigeration