Integrating access control policy specification into the software development process
Full text
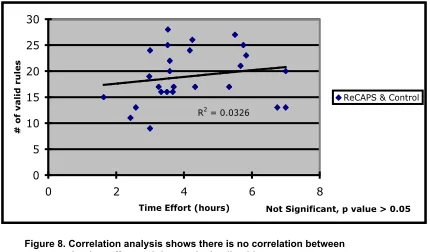
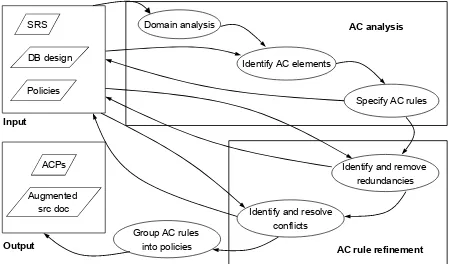
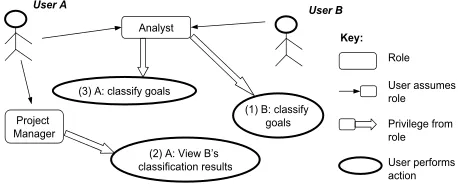
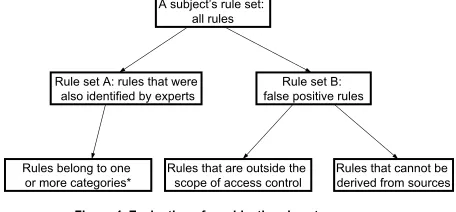
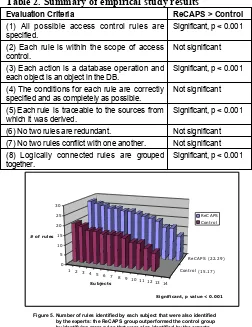
Figure
Related documents
ในกรณีที่ผู้เล่นก าลังจะพิจารณาว่าจะขอ Challenge หรือไม่ ผู้เล่นฝ่ายที่ขอ Challenge
The malERA Drugs Consultative Group brought together malaria biologists, drug developers, clinical investigators, and control officials, and consulted outside experts on drug
The JMA physicians’ liability insurance covered the liability of individual Class-A members, but payments for the liability of non-member physi- cians were cut, and there was a rush
• Supervisor M disguised his identity by logging into Facebook using a friend’s account, searched the Facebook sites of various employees, and accessed one employee’s site who
As at 31 December 2012, NOMOS served approximately 13,500 corporate customers, 85,800 small business clients and approximately 1.5 million retail customers, including private
Now, while all parts of the body are capable of sending positive and negative signals, the head (including the eyes and mouth) is under the closest scrutiny.. Most good
The main tasks in 2004 consisted in (a) recovering the 6 floats which had been drifting at surface for about 6 weeks between May 12 and June 21, 2004, (during this whole period,
This paper proposes a conceptual framework for integrating Sarbanes- Oxley compliance needs into the software development process by mapping the various stages of the