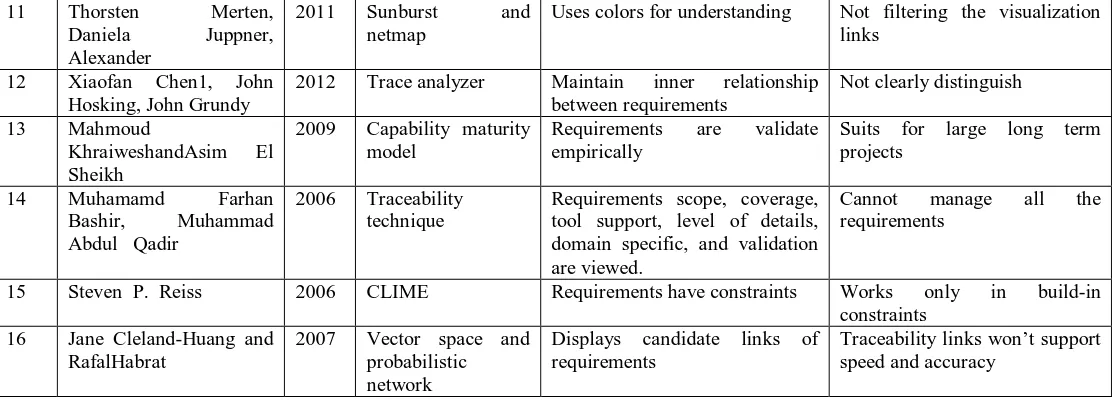
Study on Requirement Engineering and Traceability Techniques in Software Artefacts
Full text
Figure
Related documents
FIGURE 3 Pregnant women who delivered and received a complete or incomplete ANC package at the Ruby Medical Centre, Kiambu, Kenya, 2007–2013.. † Number of ANC visits was known
The JMA physicians’ liability insurance covered the liability of individual Class-A members, but payments for the liability of non-member physi- cians were cut, and there was a rush
All data in this report belong to publishers indexed in the Book Citation Index by Thomson Reuters.. Engineering
SAA SYSTEMS APPLICATIONS ARCHITECTURE SAA/CUA SAA / COMMON USER ACCESS SAC SCRIPTOMATIC ADDRESSING COMPUTER SAC STORAGE ACCESS CONTROL. SAC STORAGE ACCESS CHANNEL SAC STORE AND
• Shift economic empowerment activities away from the micro enterprises to the ‘educated risk takers’, and provide comprehensive business development support services to
Look at the table below. According to Reading Passage 1, to whom or what do the phrases on the right refer? Write your answers in boxes 5 -11 on your Answer Sheet. The first one
This report and corresponding data visualizations and data stories attempt to fill gaps and support local discussion about employment trends for graduates of academic programs at
Now, while all parts of the body are capable of sending positive and negative signals, the head (including the eyes and mouth) is under the closest scrutiny.. Most good