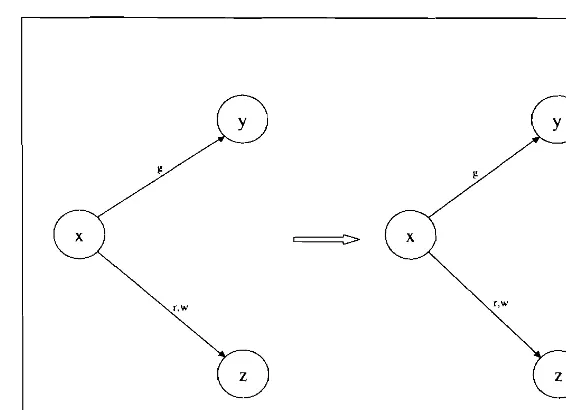
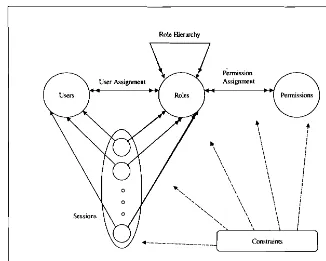
User access control and security model
Full text
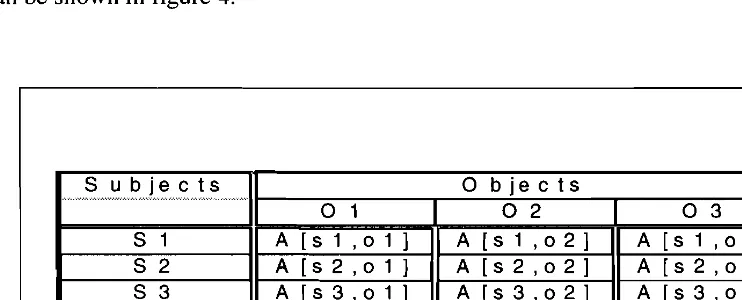
Figure
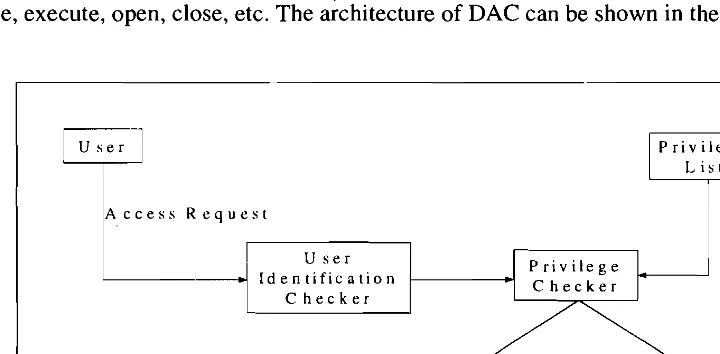
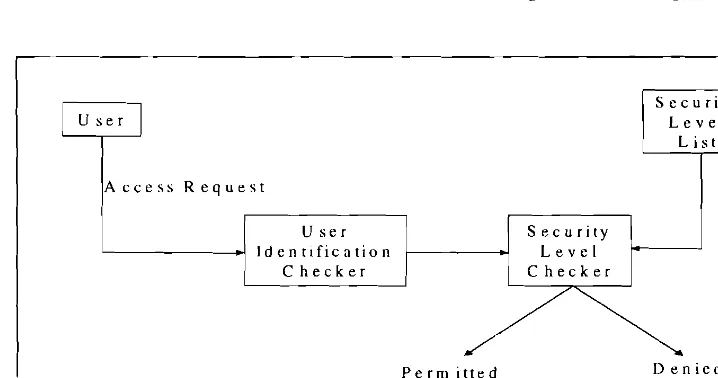

Related documents
Our results show that the significant native-immigrant wage gap that exists both in terms of average wages and of differentials along the wage distribution is
State Agency Strategic Plans Council On Virginia’s Future (Long-term/Statewide) Management Agreements Management Scorecard Virginia Results Agency Goals & Performance
Evidence of Effectiveness APRI focused on answering several key questions about the program’s effective- ness by collecting data on attendance rates (year-end attendance), number
The USCG can access the EDS to support other missions and new data is being added to the systems such as ice cover, atmospheric conditions, wave conditions, and in-water
Aboubakari Babamousa, Director of Department of Infrastructure &Energy, African Union Commission (AUC) Jamal Saghir, Senior Regional Advisor, Africa of The World Bank.
VA mental health services are available in specialty clinics, primary care clinics, nursing homes, and residential care facilities where Veterans receive health care.. Specialized
In this document we proposed to build a Configuration Management Database and how to implement an ITIL Change Management process, including the development of a prototype to support
However, these points are not reliable enough to be used in ICP registration if the capture points are far from each other because two possible sources of errors exist: errors in