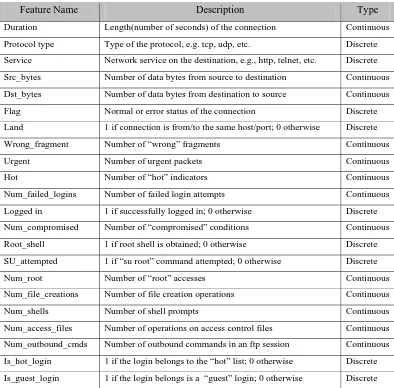
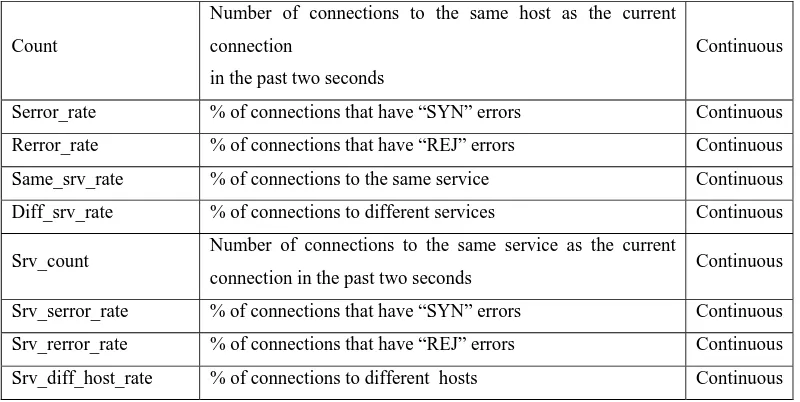
Anomaly network intrusion detection method in network security based on principle component analysis
Full text
Figure
![Figure 1. Dividing projection distance into two states [4]](https://thumb-us.123doks.com/thumbv2/123dok_us/1285050.1161004/3.612.211.403.291.422/figure-dividing-projection-distance-states.webp)
Related documents
The use of a work tool attachment point to handle/lift objects, could affect the machine lift performance. Lift capacity stays within ± 5% for all available
• Fare clic per modificare gli stili del testo dello schema " – Secondo livello" • Terzo livello " – Quarto livello " » Quinto livello
Cloud service QoS prediction aims at making personalized QoS value prediction for the service users by employing the partially available information (e.g., QoS
Ironically, to some extent, the shift from capital to benefits may have protected housing spending in recent years, resulting in a less steep drop in public sector house
Apart from services provided by SDC, MahaOnline is also providing various services as below. 1) Software as a Service (SaaS) 2) BI as a Service (BIaaS) 3) GIS as a Service (GISaaS)
The study focuses on the relationship between employee engagement (vigour, absorption and dedication) and organisational commitment (affective commitment, continuance commitment and
Among them are the following: (1) Collaborative Researches was done through mentoring, thereby increasing the involvement of junior researchers to do research; (2) Awareness and
Learning from the examples of successful blogs by elementary teachers, four common types of classroom blogs with accompanying examples are shared: Classroom News Blogs, Mirror Blogs,