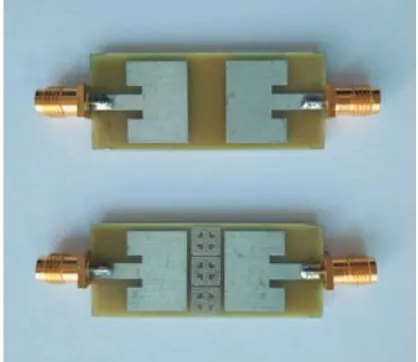
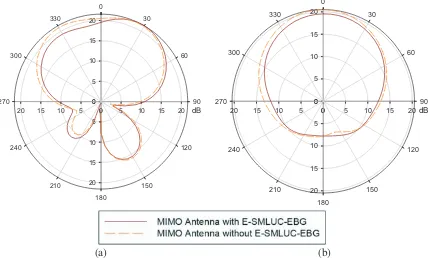
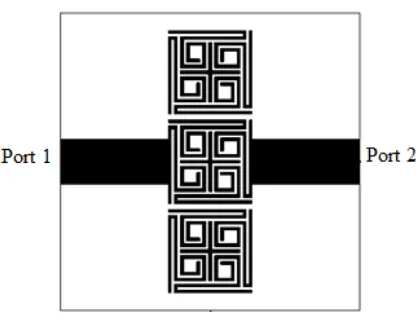
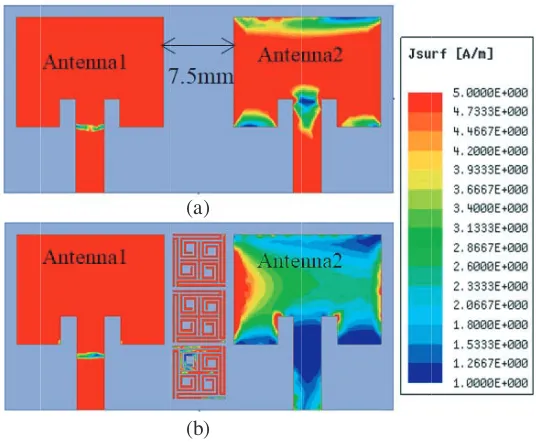
MIMO Antenna Mutual Coupling Reduction for WLAN Using Spiro Meander Line UC-EBG
Full text
Figure
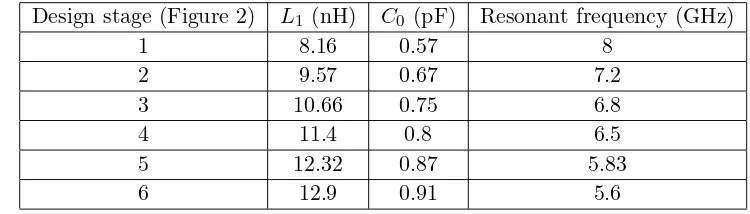
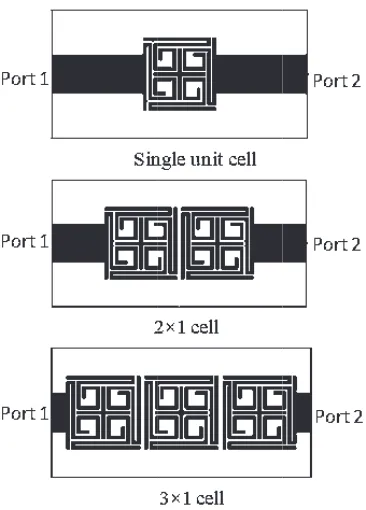
Related documents
TABLE 7: Mean Scores for High and Low Competence and Motivation Participants on Interdependence Scale (for Heritage Culture Prime) and Independence Scale (for Host Culture Prime
Based on results of a simulation, use of this suggested algorithm in time sharing and real time systems will result as increase in performance of the systems by decreasing
In future, we will grow new strategies and calculations for finding continuous examples over information streams which beats the disadvantages of the existing
(2007) showed that home-schooled students are able to adjust to the college environment.. and are
Teleost fish maintain a greater number of nuclear receptors (NRs) compared to other vertebrates due to a third genome duplication specific to their lineage (3R).. The retention
KEYWORDS dinB ; Escherichia coli ; adaptive mutation; copy number variant; error-prone polymerase; gene ampli fi cation; lactose operon; local over- replication; mutagenesis; plasmid..
Figure 3 represents the ge- netic map of the major two-way epistatic QTL, which are Figure 2 Marker effects estimated in days as posterior means for the fl owering time trait with
While the DSR protocol has a secure version ARIADNE [16], which employs symmetric key cryptography to provide security to the source routing process.. However,