Linux
Utilities
for
IBM
System
z
Installing
and
using
the
webScurity
webApp.secure
client
Linux
Utilities
for
IBM
System
z
Installing
and
using
the
webScurity
webApp.secure
client
Note
Beforeusingthisinformationandtheproductitsupports,readtheinformationin“Notices,”onpage19.
FirstEdition(August2006)
©CopyrightInternationalBusinessMachinesCorporation2006.Allrightsreserved.
USGovernmentUsersRestrictedRights–Use,duplicationordisclosurerestrictedbyGSAADPScheduleContract withIBMCorp.
Contents
About
this
book
.
.
.
.
.
.
.
.
.
.
. v
Chapter
1.
Overview
.
.
.
.
.
.
.
.
. 1
Chapter
2.
Pre-requisites
.
.
.
.
.
.
. 3
Chapter
3.
Installation
.
.
.
.
.
.
.
.
. 5
Chapter
4.
Configuration
.
.
.
.
.
.
. 7
Initialization . . . 8
Testingtheconfiguration . . . 8
Backinguptheconfiguration . . . 8
Chapter
5.
Operation
.
.
.
.
.
.
.
.
. 9
Userinterface . . . 9
Chapter
6.
Security
.
.
.
.
.
.
.
.
. 11
Chapter
7.
Data
integrity
considerations
.
.
.
.
.
.
.
.
.
.
. 13
Chapter
8.
Tuning
.
.
.
.
.
.
.
.
.
. 15
Chapter
9.
Service
and
upgrade
.
.
.
. 17
Obtainingupdates . . . 17
Appendix.
Notices
.
.
.
.
.
.
.
.
.
. 19
About
this
book
Thisdocumentdescribeshow tosetupandusethewebScuritywebApp.secure componentinthecontextofLinux®Utilities forIBM®Systemz™(LinuxUtilities). LinuxUtilities areasuiteofLinuxsolutions configuredandtestedonSystemz in a z/OSandLinuxworkloadscenario.LinuxUtilitiesprovidespecific infrastructure functionsthatarecomplementary tofunctionsonz/OS.WithLinuxUtilities you haveanadditionaloption tooptimizeyour z/OSenvironment.LinuxUtilitieshelp toprovidequickdeployment,easyinstallation,andreducedtime-to-marketof infrastructurefunctionswithminimalimpactonz/OSskillsandresources. For moreinformationonLinuxUtilitiesvisitwww.ibm.com/zseries/os/linux/ utilities. Onthis siteyoumightalso findupdatestothisdocument.
For informationonrunningLinuxonSystemzmainframessee:
v
z/VMandLinuxonIBMSystemz:The VirtualizationCookbookforSLES9,SG24-6695
v z/VMandLinuxonIBMSystemz:The VirtualizationCookbookforRed HatEnterprise
Chapter
1.
Overview
ThewebScurity® webApp.secure®client forLinuxonSystemz protectsweb application serversrunningonIBMsystemsunderz/OS®fromwebapplication attackswhichtakeadvantageofthestatelessnatureoftheWebprotocol(HTTP). Theclient stopsindiscriminateHTTPwormorvirusattacks,andalso discriminate targetedInternet attacksdirectedattheapplicationsourcecode.
Even whenprotectedbya generalfirewall,webapplicationsarestill vulnerableto criticalattackssuchasSQLinjection,cross-sitescripting,cookiepoisoning,hidden fieldmanipulation, andothers.ThewebScuritywebApp.secure clientoperates invisiblyandprotectstheapplicationbyexaminingtheHTTPnetworktrafficto ensurethatit conformstoIntendedUseGuidelinesspecifiedforthesite. Thefunctionsprovidedbytheutilityinclude:
v Provisionofatrusted gatewaythatprotectsall webapplicationcode,z/OS,
WebSphere®or othermiddleware andtheirvulnerabilities,
v Checkingof webcontentinthede-militarisedzone(DMZ)withnorisktothe
applicationserversrunningonz/OS,
v Set&Forgetcontrolsthatautonomically deriveandupdatepolicy,
v Anaddedlayerofregulatory compliancethatexceeds governmentguidelines
forGLBA,HIPAAand SOX,
v Isolationofz/OSfromInternet trafficandthreats,usingHiperSockets
™forfast communicationsthatare physicallysecure.
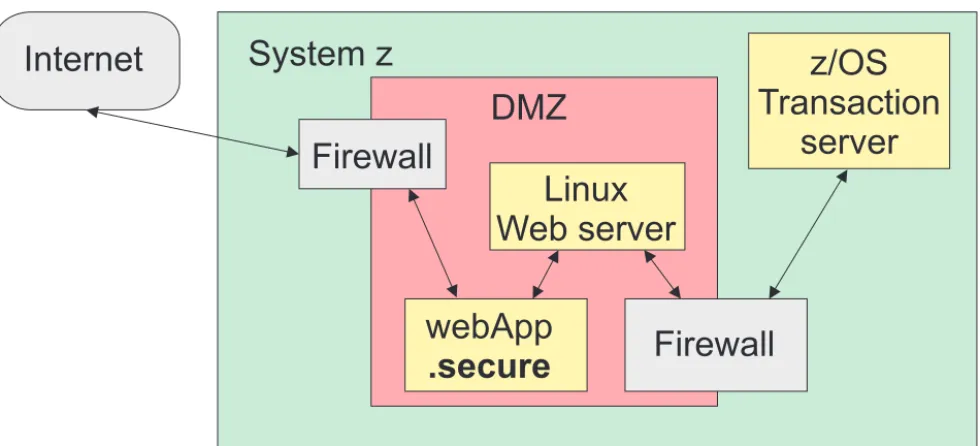
Asshown inFigure1, webApp.securerunsintheDMZbetweentheexternal firewalland theLinuxwebproxy.Afterthepackagingof networktraffichasbeen verifiedbytheexternal firewall,and beforethetrafficispassed throughthe internalfirewalltothez/OSapplication,thecontentsofthetrafficareverifiedby webApp.secure.
Internet
System z
DMZ
Transaction
z/OS
server
Linux
Web server
webApp
.secure
Firewall
Firewall
Thiscanbeusedasastartingpointinthetransitionfromthedistributed
environment,but themaximum benefitsfromwebApp.securecanbegainedinan environment suchasthatillustratedinFigure2.Herethenecessaryfirewall functionsare performedbyIPSecandIPSinthez/OSTCP/IPstack. Inthisway thecomplexityandexpense ofthe″choke″orprivatefirewallcanbeeliminated and increasedperformance willresult.
Internet
System z
DMZ
z/OS
Transaction
server
IPSec/IPS
Linux
Web server
webApp
.secure
Firewall
Figure2.Advancedscenario
Chapter
2.
Pre-requisites
Thissectionidentifies pre-requisitesforthewebScuritywebApp.secureclientfor LinuxonSystemz.
v Theutilitymustbe installedinto LinuxonSystemz runninginanLPAR or
underz/VM®.
v SystemRequirements– Compatibility
– All majorwebbrowsers
– All HTTPwebservers
– All HTTPapplication servers
– Fully compatiblewith HTTP1.0and1.1
– Fully compatiblewith HTML3.2and4.0,includingcascadingstylesheets
– Fully compatiblewith clientsidescriptinglanguages(JavaScript
™,VBScript, etc.)
– SSL40/128bitencryptionand globalID
v SystemRequirements– Minimum
– 128 MbytesRAMrecommended
– 300 Mbytesfreediskspacerecommended
v Ifyouhostmultiple websites onthesameserverusingIP-based virtualhosting,
thenyouwillneedtoset upaseparate instanceforeachIP.Setthe<listen-ip> property(seeChapter4,“Configuration,”onpage7) ofeachinstancetotheIP addressofeachwebsite.
Check “Obtainingupdates”onpage17for thelatestversionof thewebApp.secure client.
Chapter
3.
Installation
InstallationofthewebScuritywebApp.secureclient onSystemz
AsthewebScuritywebApp.secure clientrunsentirelyonLinuxthereisnothingto install onz/OS.
TheLinuxsoftware issupplied asa RPMpackage,forexample
webApp.secure.pe-3.0-1.s390x.rpm.ThisisinstalledinLinuxonSystemz using the rpm -i command.
Fulldetailsaregivenin thewebApp.secure Installationand SetupGuide, http://www.webscurity.com/pdfs/wa_installation_setup_guide.pdf.More informationaboutinstallationonLinuxorUNIX®iscontainedinthedocument
Chapter
4.
Configuration
How toconfigurewebApp.secureonz/OSandonLinuxonSystemz.
Configurationonz/OSwillgenerallybe unnecessary.Theonlyexceptionwouldbe if webApp.secureisrequiredto monitorwebaccessoriginatinginz/OS.Inthis caseitisnecessarytomodifytheroutingtableonz/OStodirectthenettraffic through thewebApp.secureclient.Theoriginalroutingtableentriesare usedin theconfigurationoftheutilityonLinux.
ThewebScuritywebApp.secureclientisconfiguredonLinuxinaset ofXMLfiles whichare maintainedwith theuseofatexteditorsuchasvi.Thefirstofthese files isthelocationsfile,etc/wa.conf.Thisfileholdsapointer tothemain
configurationsettingsinproperties_file,aswellaspointerstologfilesandflags forlogsettings.BasicdetailsaregiveninthesectionToInstallwebApp.secure on LinuxinthewebApp.secureInstallationandSetupGuide,http://
www.webscurity.com/pdfs/wa_installation_setup_guide.pdf.
Thedefaultlocationforthepropertiesfileis/usr/local/wa/etc/WAProperties.xml.The principle entriesinthis filearetheweb-server-name,web-server-port,listenport, and host-namewhichidentifythewebservertobeprotected. Otherentriesmaybe addedto definepoliciesand detectionsettings.
Theformatsof theprincipalentriesare: Web ServerName
<web-server-name>server_ip_address</web-server-name> forexample:
<web-server-name>our.server</web-server-name> or:
<web-server-name>192.168.0.2</web-server-name>
ThisistheinternalreferenceofthewebserverwebApp.secure isprotecting.Itis typicallyanIPaddressoran internalservername.
Web ServerPort
<web-server-port>server_port</web-server-port> forexample:
<web-server-port>8080</web-server-port>
IfwebApp.secureisrunningonthephysicalwebserverthisshouldbea non-standard portnumber.However,ifthey arerunningonseparate machines, this canbeanyvalidTCPportnumbernotaccessiblefromtheoutside.
Listen IP
<listen-ip>ip_to_monitor</listen-ip> forexample:
ThisisanoptionalIPaddressthatwebApp.secure shoulduse. IfnoIPisspecified, webApp.securewilluseallavailable.
Listen Port
<listen-port>normal_port</listen-port> for example:
<listen-port>80</listen-port>
ThisistheTCPportnumberwebApp.securewilluseforunencryptedtraffic. Normally thiswillbethestandardHTTPport80.
Host Names <host-names>
<host-name>host</host-name> <host-names> for example: <host-names> <host-name>www.maindomain.com</host-name> <host-name>www.subdomain.com</host-name> <host-names>
Theseareoneormore fully-qualifiedexternalhostnamesofthewebsites
webApp.secureisprotecting.Addanentryforeveryname-basedvirtualwebsite hosted onthewebserver.
Full detailsofthese fieldsandotherconfigurationsettingsaregiveninthe documentWelcometowebApp.secure,/usr/local/wa/doc/Welcome_unix.pdf.
Initialization
The webApp.secureprocessisstartedwiththecommand/usr/local/wa/bin/wa. Thiswillnormallybe addedtoasystemboot procedure.Nofurtherinitialization isrequired.
Testing
the
configuration
TestingthatthewebScuritywebApp.secureclienthasbeensuccessfullyconfigured. The configurationcanbetestedbyfollowingtheexamples giveninthe
Testing/Experimenting sectionofthewebApp.secureInstallationandSetupGuide, http://www.webscurity.com/pdfs/wa_installation_setup_guide.pdf,and the
EvaluationInstallationExamplessectionintheWelcometowebApp.securedocument,
/usr/local/wa/doc/Welcome_unix.pdf.
Backing
up
the
configuration
BackinguptheconfigurationsettingsofthewebScuritywebApp.secureclient The configurationsettingsareheld intextformatinanXMLfileanda conffile (seeChapter4,“Configuration,”onpage7 fordetails.)Thisfileshouldbe backed upbycopyingittoasecurelocationwheneveritismodified.Restorationissimply a matterof copyingitbackagain.
Chapter
5.
Operation
How tousethewebScuritywebApp.secureclient
webApp.secureoperatesinvisiblyintheSystemz DMZ,byprotectingeachURL within aSystemz machinewith“Set &Forget”controlsthatautonomicallyderive and updatewebsitepolicyascontentexitsthewebserver.ThewebApp.secure Administration ConsolerecordsandreportsstatisticsforallHTTPdaemon requests,showingtotalallowedandtotalblockedbyattackattempttype.
User
interface
ThewebScuritywebApp.secureclientforLinuxonSystemziscontrolledusing thebrowser-basedAdministrationOption.
Examplescreens fromtheAdministrationOptioncanbefoundfromthe http://www.webscurity.com/products.htm page,byfollowingthe″QuickStart Guide″link.
TheRemoteAdministration propertygroupallowsyoutospecifyparametersfor browser-based administration.Therearesafeguardstolimit accessibilitytothe remote administrationfeature,anditdoesuseSSL(https://),but itwasdesigned tobe usedoveranintranet.Theparametersare:
<remote-admin>
<enable>status</enable> </remote-admin>
forexample: <remote-admin>
<enable>true</enable> </remote-admin>
Setto“True”toenablebrowser-basedadministration.
<remote-admin>
<listen-ip>ip_to_monitor</listen-ip> </remote-admin>
forexample: <remote-admin>
<listen-ip>192.168.0.2</listen-ip> </remote-admin>
Thisisthespecific IPaddresswebApp.secureshoulduseforbrowser-based administration.
Ifleft blankallavailable IPaddresseswillbeused.
<remote-admin>
<listen-port>normal_port</listen-port> </remote-admin>
<remote-admin>
<listen-port>8020</listen-port> </remote-admin>
ThisistheTCPportnumberwebApp.secureshoulduseforbrowser-based administration.
<remote-admin>
<password>password</password> </remote-admin>
for example: <remote-admin>
<password>admin</password> </remote-admin>
Thisisaone-wayhashedpasswordtouseforbrowser-basedadministrationaccess. Note: Thedefaultpasswordis“admin”andcanonlybechangedfromthebrowser
whenthisoption isenabled.
<remote-admin> <client-ips>
<client-ip>client_ip</client-ip>
</client-ips> </remote-admin> for example: <remote-admin> <client-ips> <client-ip>192.168.0.105</client-ip> </client-ips> </remote-admin>
Theseareoneormore clientIPaddressesthatareallowed toconnectto webApp.secureforbrowser-basedadministration.
IfnoIPs arespecifiedconnectionswillbe acceptedfromanyIPaddress. Example addressingfroma browser:
https://192.168.0.2:8020/
(Pleasenotetheuseofhttps inthisexample.)
Chapter
6.
Security
Data securityisachievedwhenusingthewebScuritywebApp.secureclientfor LinuxonSystemz.
webApp.secureprotectsallelementsofthewebenvironmentincludingoperating system,HTTPdaemon,developmentanddeploymentframework, andDBMS. It also ensuresthatwebsites,theirapplications,and theirassociateddatabasesare accessedand usedexactlyasintended,witha positivemodel,byenforcingweb siteguidelines,rulesandpolicy.
Websitepolicyisautomaticallysecuredafter webApp.securemapstheweb application businesslogic,includingvulnerabilities(forexamplelegacyand new application software),uponinstallationandautonomicallyderivesandupdates policyascontentexits theserver.
webApp.secureisawebapplicationfirewall,residingintheDMZbetweenthe standardfirewallandtheLinuxwebserver,andprotectsagainstattacksseeking to exploitsoftwarevulnerabilitiesthrough:
v SQLinjection,
v Cross-sitescripting,
v Hiddenfieldmanipulation,
v Cookiepoisoning,
v Stealthcommanding,
v Forcefulbrowsing,
v Bufferoverruns,and
Chapter
7.
Data
integrity
considerations
EnsuringdataintegritybetweenthewebScuritywebApp.secureclientforLinuxon Systemz andz/OS.
Data integrityisautomaticallyassuredbyvalidationwith websitepolicywhenthe HTTPstreampassesthrough astandardfirewall,andautonomicallyuponexit fromthewebserver.
Chapter
8.
Tuning
TuningthewebScuritywebApp.secure clientforLinuxonSystemz. Tuningonz/OSisnotapplicable;alltuningisperformedonLinux. Theparameterswhichcanbemodifiedtoadjusttheperformanceof webApp.secureforLinuxonSystemzare:
<max-connections></max-connections>
Themaximum numberofsimultaneousclientconnectionsthatwillbe served.Once thethresholdisreachedtheoperatingsystem’slistenqueue willbeused.
<max-listen-queue></max-listen-queue>
Themaximum numberofpendingconnectionsthatwillbe servedfromthe operatingsystem’slistenqueue.
Chapter
9.
Service
and
upgrade
Migrating tothelatestversionofthewebScuritywebApp.secureclientforLinux onSystemz.
ThiswillnormallybeperformedbydownloadingandinstallingthelatestRPM fromwebScurityasdescribedinChapter3,“Installation,” onpage5. Installation willreplacetheexecutable/usr/local/wa/bin/waexecutablewiththelatest webApp.secureversion(currentlyversion4.0).
Thetasks toperformare: 1. Shut downwebApp.secure,
2. Copytheexecutable,
3. StartwebApp.secure.
Obtaining
updates
ObtainingfixestothecurrentreleaseofthewebScuritywebApp.secureclient,and acquiring anewrelease
Thelatest versionofthewebScuritywebApp.secureclientcanbedownloaded fromhttp://www.webscurity.com/download.htm
Appendix.
Notices
Thisinformationwasdevelopedforproductsandservices offeredintheU.S.A. IBM maynotoffertheproducts,services,orfeaturesdiscussedinthisdocumentin othercountries.Consultyour localIBMrepresentativeforinformationonthe productsand servicescurrentlyavailableinyourarea.Anyreferencetoan IBM product, program,orserviceisnotintendedtostateorimplythatonlythatIBM product, program,orservicemaybe used.Anyfunctionallyequivalentproduct, program, orservicethatdoesnotinfringeanyIBMintellectualpropertyrightmay be usedinstead.However, itistheuser’sresponsibility toevaluateandverifythe operationofanynon-IBMproduct,program, orservice.
IBM mayhavepatentsorpendingpatent applicationscoveringsubjectmatter described inthisdocument.Thefurnishingofthisdocumentdoesnotgrantyou anylicensetothesepatents.Youcansend licenseinquiries,inwriting,to: IBM DirectorofLicensing
IBM Corporation North CastleDrive Armonk,NY10504-1785 U.S.A.
For licenseinquiriesregardingdouble-byte(DBCS)information,contacttheIBM IntellectualProperty Departmentinyourcountryorsendinquiries,in writing,to: IBM WorldTradeAsiaCorporation
Licensing
2-31 Roppongi3-chome,Minato-ku Tokyo106-0032,Japan
Thefollowingparagraphdoesnotapplyto theUnited Kingdomor anyother country wheresuchprovisionsareinconsistentwithlocallaw:
INTERNATIONALBUSINESSMACHINESCORPORATIONPROVIDES THIS PUBLICATION“ASIS”WITHOUT WARRANTYOFANYKIND,EITHER EXPRESSORIMPLIED,INCLUDING,BUTNOTLIMITED TO,THEIMPLIED WARRANTIESOFNON-INFRINGEMENT,MERCHANTABILITYORFITNESS FORAPARTICULARPURPOSE.Somestatesdo notallowdisclaimerofexpress or impliedwarrantiesincertaintransactions,therefore,thisstatementmaynotapply toyou.
Thisinformationcouldinclude technicalinaccuraciesortypographicalerrors. Changes areperiodicallymadetotheinformationherein;these changeswillbe incorporatedinneweditionsof thepublication.IBM maymakeimprovements and/or changesintheproduct(s)and/ortheprogram(s)describedinthis publication atanytimewithoutnotice.
Anyreferencesinthisinformationtonon-IBMWebsitesareprovidedfor
convenienceonlyanddonotinanymannerserveasanendorsementofthoseWeb sites.Thematerialsat thoseWebsitesarenotpartof thematerials forthisIBM productanduseofthoseWebsitesisatyour ownrisk.
IBM mayuseordistribute anyoftheinformationyousupplyinanywayit believes appropriatewithoutincurringanyobligationtoyou.
Licensees ofthisprogramwhowishtohaveinformationaboutit forthepurpose of enabling:(i)theexchangeofinformationbetweenindependentlycreated programs andotherprograms(includingthis one)and(ii)themutualuseofthe informationwhichhasbeenexchanged,shouldcontact:
IBM Corporation
SoftwareInteroperabilityCoordinator,Department49XA 3605Highway52N
Rochester,MN55901 U.S.A.
Such informationmaybeavailable,subjecttoappropriatetermsandconditions, includinginsomecases,paymentof afee.
The licensedprogramdescribedinthis informationandalllicensedmaterial available foritareprovidedbyIBMundertermsoftheIBMCustomerAgreement, IBM InternationalProgramLicenseAgreement,oranyequivalentagreement betweenus.
Anyperformancedatacontained hereinwas determinedinacontrolled
environment.Therefore,theresultsobtained inotheroperatingenvironmentsmay vary significantly.Somemeasurementsmayhavebeenmadeondevelopment-level systemsandthereisnoguaranteethatthesemeasurementswillbethesameon generallyavailable systems.Furthermore,somemeasurementsmayhavebeen estimatedthrough extrapolation.Actualresultsmayvary.Usersof thisdocument shouldverifytheapplicabledatafortheirspecific environment.
Informationconcerningnon-IBMproductswasobtained fromthesuppliers of those products,theirpublished announcementsorotherpubliclyavailablesources. IBM hasnottestedthoseproductsandcannotconfirmtheaccuracy of
performance, compatibilityoranyotherclaims relatedtonon-IBMproducts. Questionsonthecapabilitiesofnon-IBMproductsshouldbe addressedtothe suppliers ofthoseproducts.
All statementsregardingIBM’sfuturedirectionorintentaresubjecttochangeor withdrawal withoutnotice,andrepresentgoalsandobjectivesonly.
Thisinformationisforplanningpurposesonly.Theinformationhereinissubjectto changebefore theproductsdescribed becomeavailable.
Thisinformationcontainsexamples ofdataandreportsusedindailybusiness operations.Toillustratethemascompletelyaspossible,theexamples includethe namesof individuals,companies,brands,and products.Allofthesenamesare fictitiousand anysimilaritytothenamesandaddressesusedbyanactualbusiness enterpriseisentirelycoincidental.
Ifyouareviewingthisinformationsoftcopy,thephotographsand color illustrations maynotappear.
Trademarks
The followingtermsaretrademarksofInternationalBusinessMachines Corporation intheUnitedStates,othercountries,orboth:
HiperSockets IBM
System z
WebSphere z/OS z/VM
All Java-basedtrademarksare trademarksofSunMicrosystems, Inc.intheUnited States, othercountries,orboth.
Linuxisa trademarkofLinusTorvaldsintheUnitedStates,othercountries,or both.
UNIX isa registeredtrademarkofTheOpenGroupintheUnitedStatesand other countries.
webScurityinc. andwebApp.secure aretrademarksofwebScurityInc.inthe UnitedStates, othercountries,orboth.
Other company,product, orservicenamesmaybetrademarksorservicemarksof others.
Readers’
Comments
—
We’d
Like
to
Hear
from
You
LinuxUtilitiesforIBMSystemzInstallingandusingthewebScuritywebApp.secureclient PublicationNo. SC33-8322-00
Overall,howsatisfiedareyouwiththeinformationinthisbook?
VerySatisfied Satisfied Neutral Dissatisfied Very Dissatisfied
Overallsatisfaction h h h h h
Howsatisfiedareyouthattheinformationinthisbookis:
VerySatisfied Satisfied Neutral Dissatisfied Very Dissatisfied
Accurate h h h h h
Complete h h h h h
Easytofind h h h h h
Easytounderstand h h h h h
Wellorganized h h h h h
Applicabletoyourtasks h h h h h
Pleasetellushowwecanimprovethisbook:
Thankyouforyourresponses.Maywecontactyou? h Yes h No
WhenyousendcommentstoIBM,yougrantIBManonexclusiverighttouseordistributeyourcommentsinany wayitbelievesappropriatewithoutincurringanyobligationtoyou.IBMoranyotherorganizationswillonlyuse thepersonalinformationthatyousupplytocontactyouabouttheissuesthatyoustateonthisform.
Name Address
Readers’
Comments
—
We’d
Like
to
Hear
from
You
SC33-8322-00
SC33-8322-00
CutorFoldAlongLine
CutorFold AlongLine FoldandTape Pleasedonotstaple FoldandTape
FoldandTape Pleasedonotstaple FoldandTape PLACE POSTAGE
STAMP HERE
IBMDeutschlandEntwicklungGmbH InformationDevelopment
Department3248
SchoenaicherStrasse220 71032Boeblingen Germany _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
___________________________________________________________________________________________________