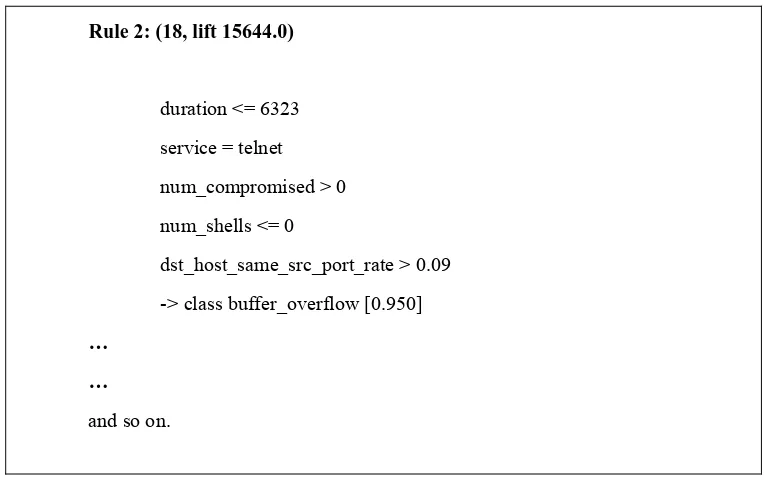
Identifying false alarm for network intrusion detection system using hybrid data mining and decision tree
Full text
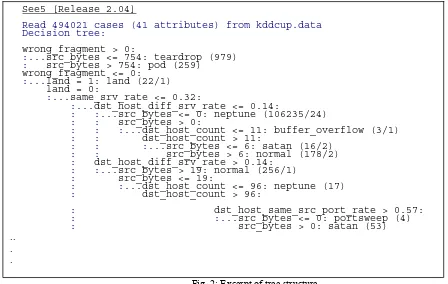
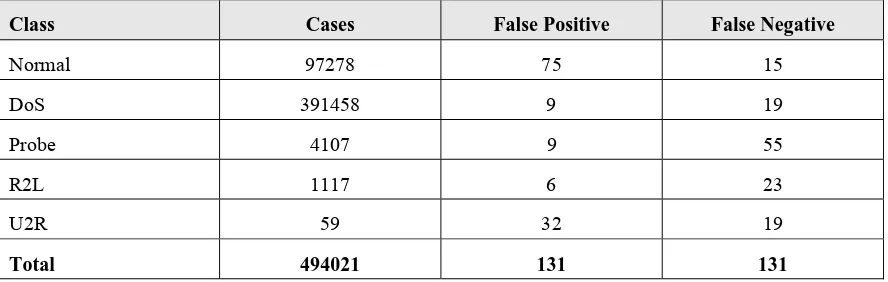
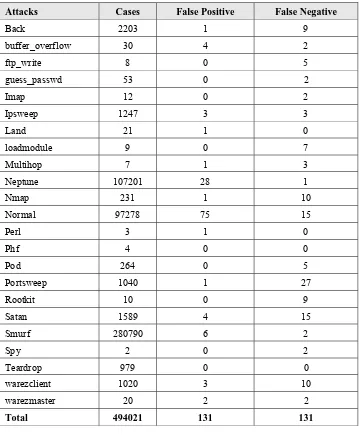
Figure

Related documents
Analog der Initialuntersuchung fanden sich bei der studienbedingten Nachuntersuchung subklinische Effloreszenzen am häufigsten im Bereich des Präputiums (16,1 %), eine
pumila plantlet through multiple shoot regeneration from stem explant cultured on MS medium supplemented with 20 µM ZEA.. Effect of different PGRs on regeneration from stem node of
The findings of this feasibility study will provide the information needed to finalise the design of a planned crossover randomised controlled trial assessing the impact of bottle
Shake (long) event Peek event Climb event.. Layered Event
As a solution, sound compensation programs help a company achieve the four main objectives of compensation: Attract, Retain, Focus, and Motivate. Designing
As such, the first ranked TTL group in Table 3 could indicate that two hosts were possibly attacking 3 207 different IP addresses (the spoofed source address being that of the target
The purpose of this study is to explore the level of resilience displayed by counseling trainees as measured by the Resilience Scale in relationship to background variables, risk
The doctors correctly predicted the length of time Maurie would live, but can you compare six weeks at home to a few months coupled to a machine in an intensive care ward. Maurie