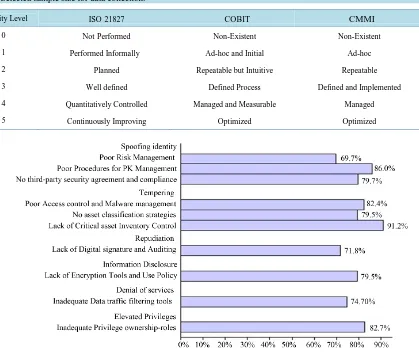
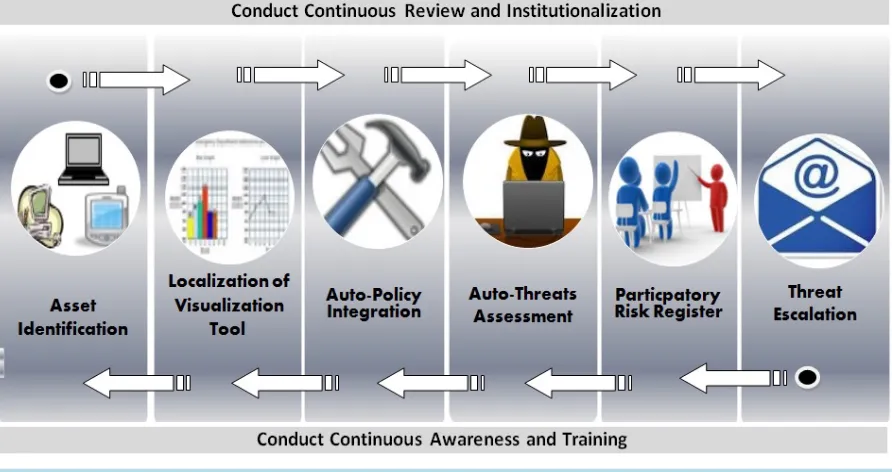
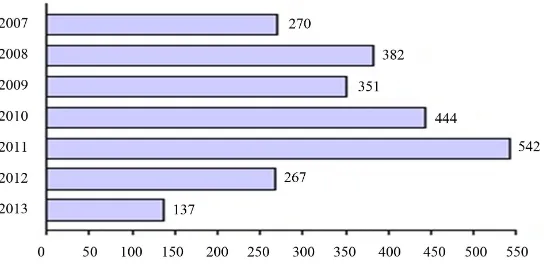
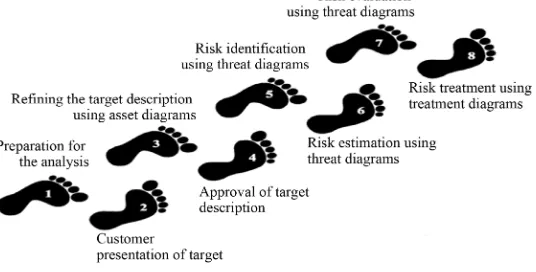
A Conceptual Framework for Threat Assessment Based on Organization’s Information Security Policy
Full text
Figure
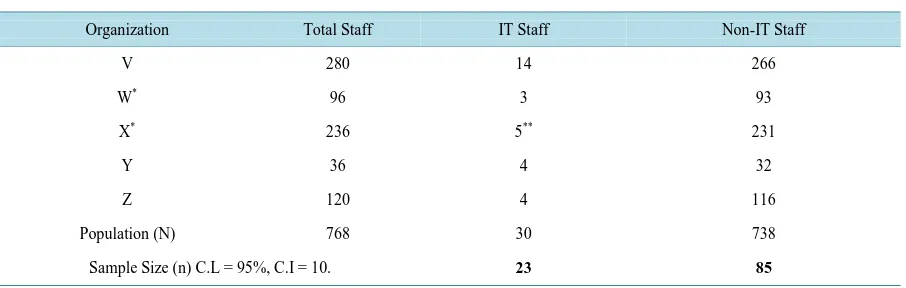
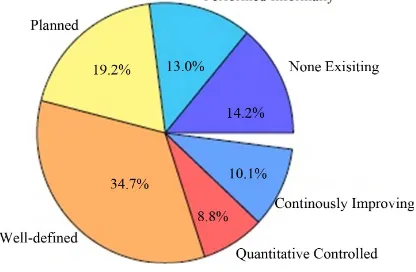
Related documents
After you have configured the VMware Application Proxy and mapped it to a vCenter Server, you can manage the agents on the VMs from the Agent Management tab in the
‣ children he had ‣ special achievements ‣ why he is remembered Create an information page about: PHARAOH CLEOPATRA. You
O objetivo deste trabalho foi avaliar a rugosidade e a molhabilidade da superfície de lâminas de madeira de curupixá (Micropholis venulosa) antes e após o processo de
Banda “Energy Losses Estimation for CPV Plants”, 6th International Conference on Concentrating Photovoltaic Systems, Freiburg, April 2010. 35 th
Petition for Exclusion: Any registered voter, representative of a political party or the Election Officer, may file with the court a sworn petition for the exclusion
This study is an attempt to explore the relationships among perceived ease of use, perceived usefulness and intention to use e-learning in the context of tertiary education and
Using the FPMW paradigm we compare the performance and eye movement behaviour of expert radiologists and novice observers (psychology students) as they search for everyday