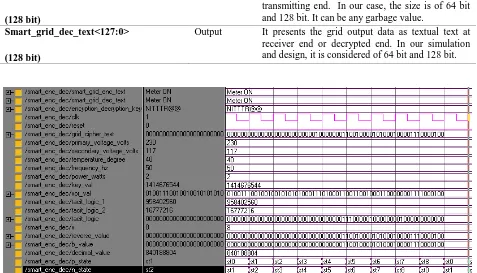
Smart Grid Security with Cryptographic Chip Integration
Full text
Figure
![Figure 1 Smart grid properties [8]](https://thumb-us.123doks.com/thumbv2/123dok_us/8416736.1692582/2.595.318.551.137.396/figure-smart-grid-properties.webp)



Related documents
represented as a six-character sequence: a reverse solidus, followed by the lowercase letter u, followed by four hexadecimal digits that encode the character’s code point..
The return value is a YAJL 'node' that represents the outermost element of the JSON document. (the
Due to these character- istics, the study’s results indicate that: (a) size of the respondent company affects the adoption of SCM prac- tices, where the larger the company, the
Composite action can be obtained with the combination of concrete and steel. Shear connectors can resist the horizontal shear and produce vertical interlocking between
In sum, the expatriate literature has overlooked the importance of continuation of spouse career in the host country and the present study brings to light the negative effect of
In our study, the closely intertwined relationships between meeting basic needs, higher risk activities, priorities and experiences on the street, and actual risky behaviors in
Smart Grid: Energy efficiency, price response, peak load.. reduction, distribution automation, new building technologies, smart metering, sensors, communication
[r]