Study on Data Security in Cloud Architecture Based on Kerberos authentication System Shital A. Salve
Full text
Figure
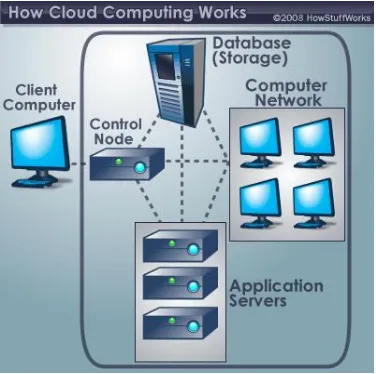
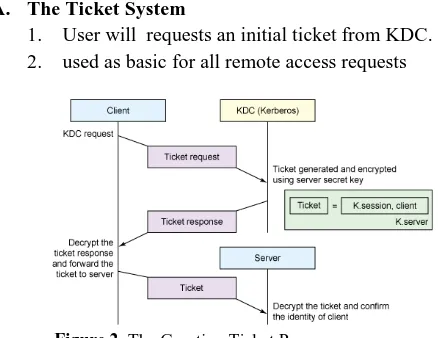
Related documents
Our key objectives and priorities for the year have been to maintain a balanced portfolio across all tumour sites and modalities and in particular to increase recruitment
THE INTERNET THE INTERNET Hybrid Clouds Public Cloud (aka multi-tenancy) Private Cloud of customer #1 Private Cloud of customer #2 Private Cloud of customer #n Extension of a
Common Deployment Models of Cloud Computing • Public cloud • Private cloud • Hybrid cloud • Community cloud 14.. Security Maturity and
Cloud services are distinguished concerning the relation between cloud provider and cloud user: ● Private clouds ● Public clouds ● Hybrid clouds ● Community Clouds Introduction
Study of relation between coping ways with individual’s characters and mental health in infertile couples who refer to Yazd infertility center.. Tehran, Tarbiat
In this paper we will discuss the service models, the different types of clouds, namely public cloud, private cloud, hybrid cloud, intercloud and their architecture
Data Security is a challenging issue of data communications today that touches many areas including secure communication channel, strong data encryption technique and trusted
Environmental factors were not considered when the quality coefficient was calculated in the previous section, and this weakens the measure as a determinant of its efficacy within the