Personal exposure to static and time varying magnetic fields during MRI procedures in clinical practice in the UK
Full text
Figure
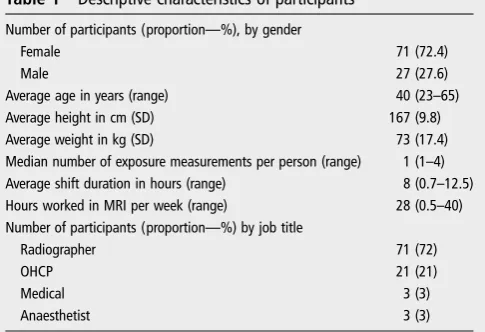

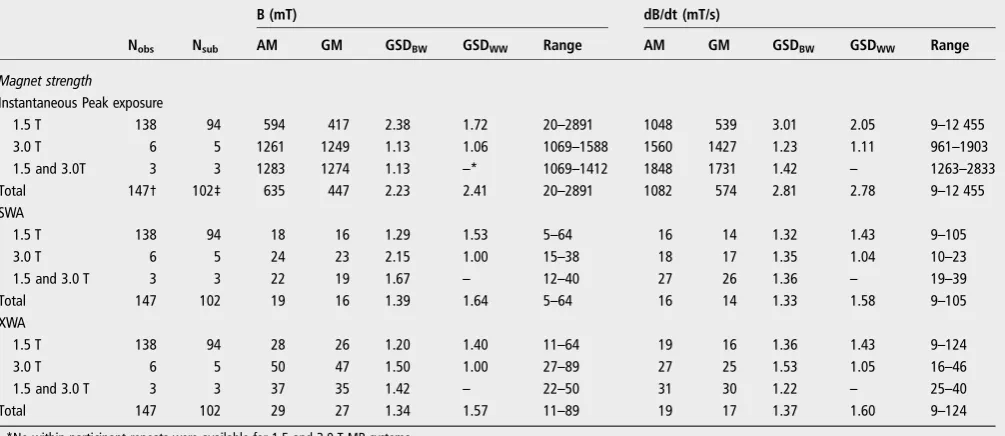
Related documents
If the bidder is not the manufacturer of the offered Computers, non‐submission of . Manufacturer's Authorization Letter(s) from the
Namely, that an integrated and sustainable International Convention on offshore structures was necessary, that fixed platforms and rig structures shall also be
Using the Statistical Cloud Model (SCM) to improve the entropy method, we establish the weight calculation model of the in- fluencing factors of dam break risk consequences..
Service Level Management DSS Operational data Server Inventory Networks Applications IT administration Performance Throughput Business Exceptions Capacity Helpdesk Da ta m o d e
Limited data indicate that the growth rates of irradiated CF-8M cast SS and Type 304L SS weld HAZ material are lower than those of wrought materials
(e) The contractor shall not be obligated to continue performance beyond the Estimated Total Hours, except that the Contracting Officer may require the contractor to
In an economy with "national" factor markets, the factor price effects of a permanent, regional specific shock register everywhere, perhaps with a brief lag. The United
To conduct our analysis we will be using the security threat model known as STRIDE: Spoofing identity, Tampering with data, Repudiation, Denial of service, and Elevation