An Efficient Technique for Finding SQL Injection using Reverse Proxy Server
Full text
Figure
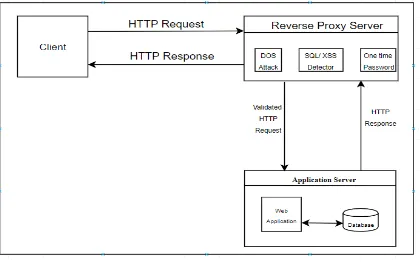
Related documents
“Man, then, as he changes place and society, nds himself in a position of discovery or understanding at ever greater depths, all of which he has in common with other men,
% Script to calculate the specific area under a Gaussian probability % density function using the Rectangular Rule?. w=0.1; % This is the width of
Ya que las penas privativas de libertad “han vivido en un constante cuestionamiento teórico y enfrentadas a la realidad de un sempiterno fracaso” (Guzmán, 2008:
There were differences by top source country with 94 per cent of Essential Skills workers from India gaining residence as a principal skilled migrant compared with 89 per cent
But also the training of model can be a problematic task: even if it can be easily performed in an ATC system (the ATC systems have a testing environment that is a copy of the
• Launch of new Private Medical Insurance System (PMI) • Launch of new General Insurance System (GIS) • Launch of new Life Insurance System (LIFE) • Development
These findings complement results from the RAND Health Insurance Experiment, a large experimental study of health care costs and utilization conducted from 1971 to 1986, to improve
Helsinki Center for Economics Research, applied microeconomics seminar, Fall 2004 Catholic University of Chile, department of economics, Fall 2004, Fall 2006, Fall 2007