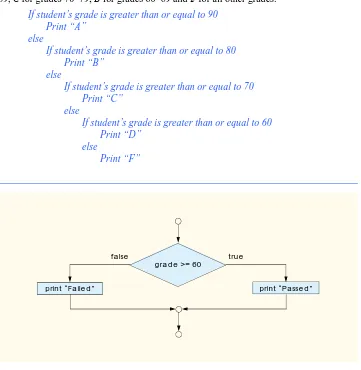
Python How to Program, 1e pdf
Full text
Figure

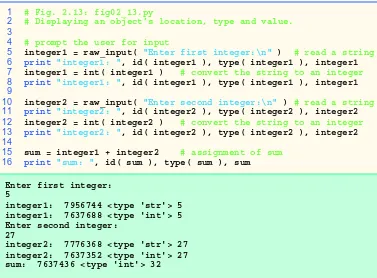
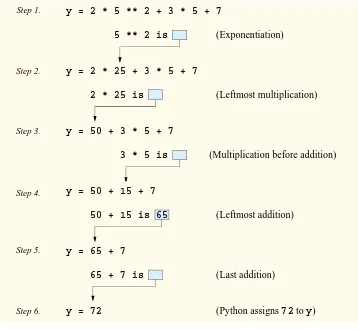
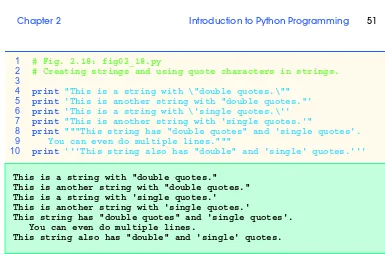
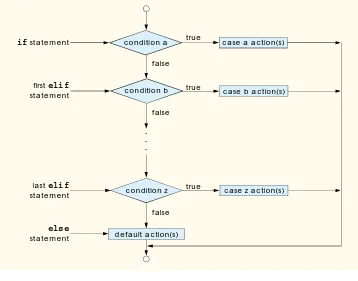
Outline
Related documents
The encryption operation for PBES2 consists of the following steps, which encrypt a message M under a password P to produce a ciphertext C, applying a
Understanding the effects of manipulations in the absence of pilot studies or previous research is important to the increasing number of studies using GC
Considering that knowledge transfer across national borders is a major advantage of MNCs (Kogut and Zander, 1993) and that the generation of knowledge and productivity spillovers
National Conference on Technical Vocational Education, Training and Skills Development: A Roadmap for Empowerment (Dec. 2008): Ministry of Human Resource Development, Department
To analyze such a large volume of data, Big Data analytics is typically performed using specialized software tools and applications for predictive analytics , data mining ,
Within the group of parents with minor children, a further distinction is made between parents with full-time residential children (>75% of the time on a monthly
Filament winding process is an expanding composite manufacturing process based on the introduction of advanced lightweight mass production items, which has increased the performance