Hydropower Development in the Lower Mekong Basin: Alternative Approaches to Deal with Uncertainty
Full text
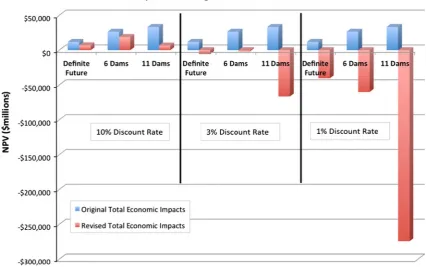
Figure



Related documents
Table 1: Students Take Charge Lessons and Groups Exposed………..19 Table 2: Steps for Data Analysis of Consumption……….…20 Table 3: Demographics of Low-income Fifth Grade
In order to cover both intentional and unintentional learning, it was decided to include the opinions of employees working in environments that focus on innovation and in
The approach taken in the AXL project is to leverage the best practices of case-method teaching and use Hollywood storytelling techniques to create fictional case
So, to begin creating a control-based modal synthesizer, we will attempt to create filter banks that replicate the frequency spectrum of sawtooth and square waves.. These filter
PROJECT COPPELIA Solver Constraints Refined Skeletal Motion Character MESH Motion ANIMATION Virtual ENVIRONMENT Performance MODELLING. Figure 1.2: T he P ro je c t “Synthesising
A comparison of the first 8 months’ data in 2005 and 2006 reveals that EU imports from China slowed down to 5.5 per cent growth rate whereas the rest of the Asian 12 countries,
The ON resistance for these geometries for the two types of devices (RON-P and RON-N) has been calculated to be 7.875 k Ω and 3.75 k Ω respectively based on experimental work
For stored attacks, it adopts a generic XSS detection using a list of known scripts in which they used a training based XSS detector in which list of all outgoing

