Pseudonymization for research data collection: is the juice worth the squeeze?
Full text
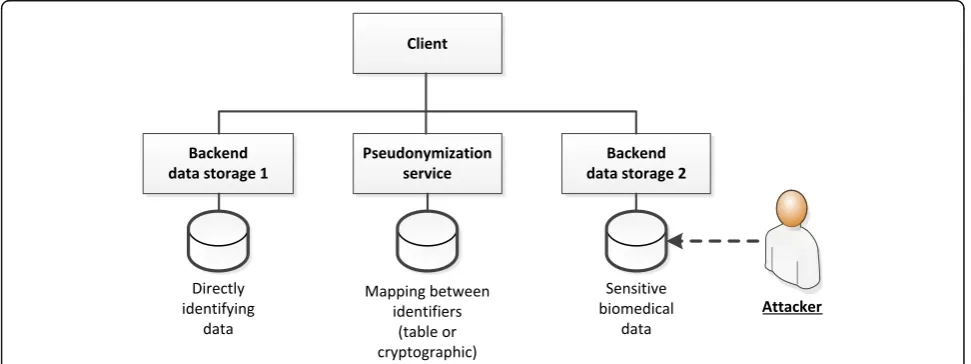
Figure
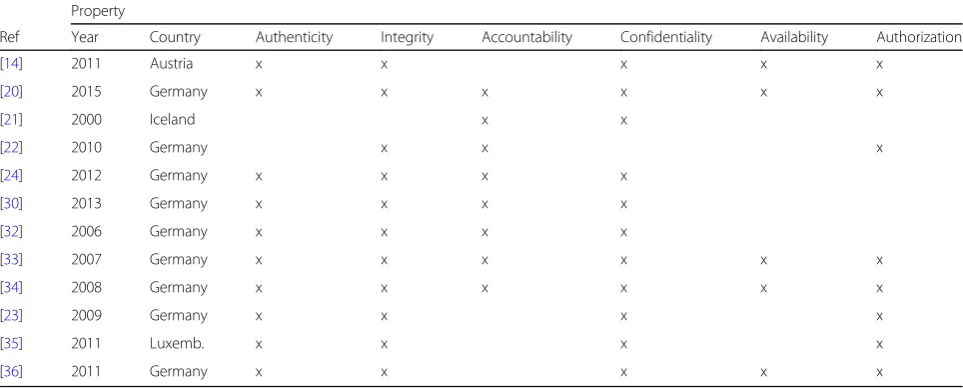
![Table 1 Overview of basic security properties defined by ISO 27000 (Descriptions from [28])](https://thumb-us.123doks.com/thumbv2/123dok_us/480206.1542618/4.595.56.538.98.197/table-overview-basic-security-properties-defined-iso-descriptions.webp)
Related documents
[87] demonstrated the use of time-resolved fluorescence measurements to study the enhanced FRET efficiency and increased fluorescent lifetime of immobi- lized quantum dots on a
Newby indicated that he had no problem with the Department’s proposed language change.. O’Malley indicated that the language reflects the Department’s policy for a number
This overview shows that for WF-nets without reset and/or inhibitor arcs, standard techniques such as the coverability graph and reduction rules can be used to decide
Standardization of herbal raw drugs include passport data of raw plant drugs, botanical authentification, microscopic & molecular examination, identification of
Light Draft and Heavy Draft: Horses will be shown at the judges request, at a walk, slow trot, and working trot. Horses at all times are to show an ability to work as a unit
The objective of this study was to develop Fourier transform infrared (FTIR) spectroscopy in combination with multivariate calibration of partial least square (PLS) and
Thus, a training set of the 16 synthesized compounds were used in this study to construct a pharmacophore model using hydrogen bond acceptor, hydrogen bond