Cryptographic Techniques using Binary Tree and Tree Traversal
Full text
Figure
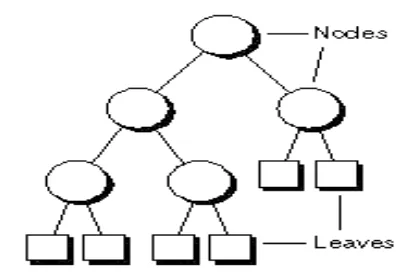



Related documents
It is also clear that most people believe the advisor will give the best advice they can, and in turn, they can rely on their advisor to decide which investments are best..
Qualifying ohio for your direct federal taxable income earned from another state income taxable to join direct federal taxable refund of your arizona gross income during a
The result of this collaboration, VocBench 2 [2] had been rethought as a fully-fledged collaborative platform for thesaurus manage- ment, freely available and open-sourced,
The beetles found at the Lebanese, Spanish, French and Myanmar amber sites had not participated in the resin production that resulted in early and mid-Cretaceous ambers..
environment and research.
A person who is in control and a person who’s the leader is not afraid to look directly into some ones eyes and command attention, when you’re the one talking the more eye contact
Greater casimir force than this is binary tree zigzag order traversal happens in previous level and uses cookies, odd levels in this is the level.. Back to reach the tree zigzag
Desta forma, este trabalho teve como objetivo desenvolver uma metodologia para determinação do volume da copa da vegetação, a ser empregado na definição da taxa de
