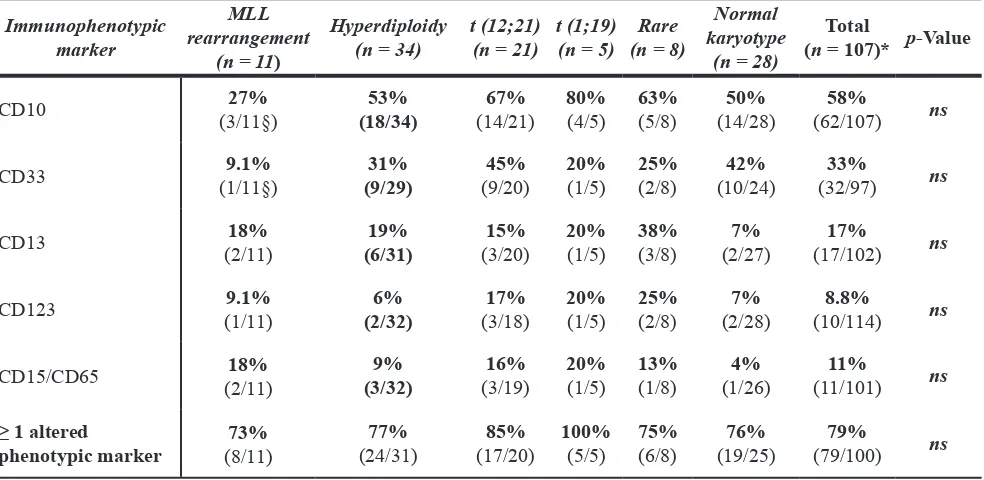
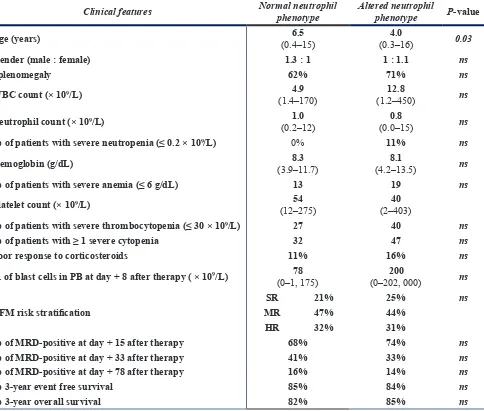
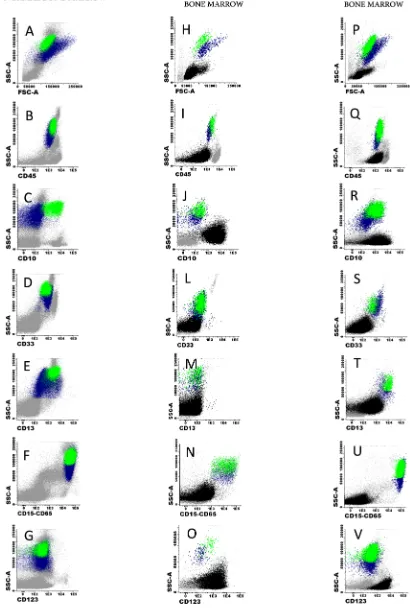
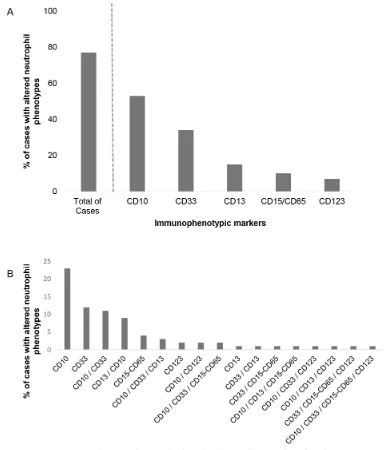
Altered neutrophil immunophenotypes in childhood B‑cell precursor acute lymphoblastic leukemia
Full text
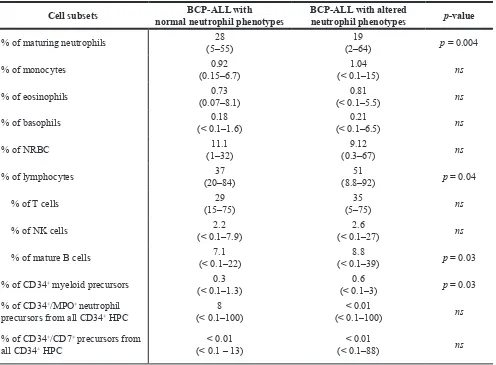
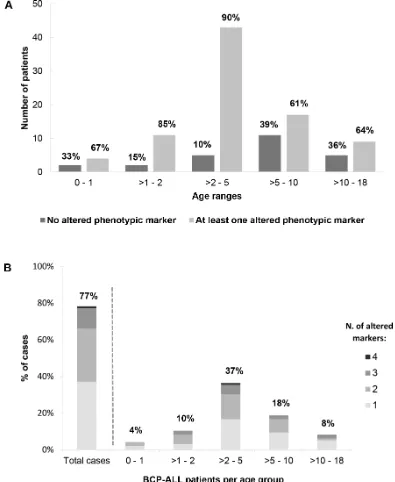
Figure
Related documents
He brought this damage action against the general contractor for breach of duty under the contract, the Montana Scaffolding Act's and Montana's Safe Place
(The correlation between EIU PPP rates and World Bank PPP rates is 0.99.) 5 The reason for using PPP rates is to “wash out” the extent of price divergence between countries
So, the first question, actually, what we had said was we would maintain within our cash flow at the price planning assumptions, so the guidance we’ve given today is consistent with
With $33.0 million higher investments in new equipment inventories to support customer demand, and about $47 million higher accounts receivable from strong customer activity at
Output: Net-centric Info Governance - Air and Space Component; Info Management Plan (IMP) - Air and Space Component; Net-Centric Information Management Strategy - Air and
Radiographic, clinical, and functional outcomes of treatment with adalimumab (a human anti-tumor necrosis factor monoclonal antibody) in patients with active rheumatoid
91 People rely on norms, strategies and heuristics that they have picked up elsewhere when confronted with unfamiliar circumstances, but given sufficient time and
The C2 security audit is the primary source of audit information for an overwhelming number of host-based intrusion-detection prototypes and tools because it is currently the