A Survey on Virtualization and Attacks on Virtual Machine Monitor (VMM)
Full text
Figure

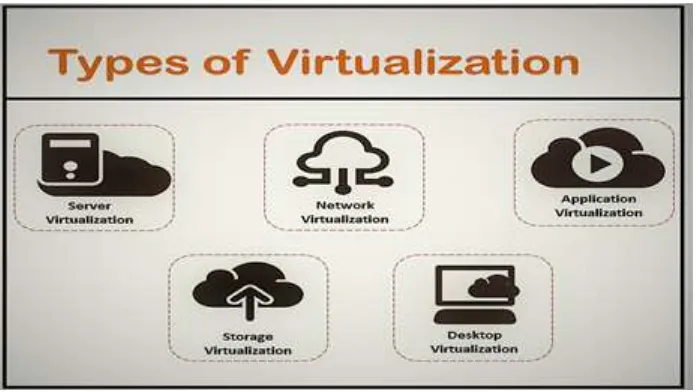
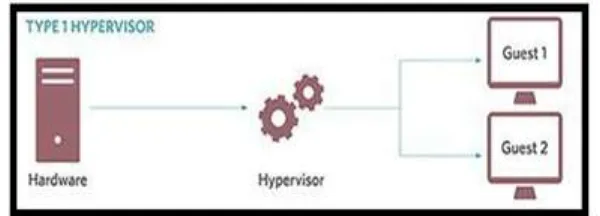

Related documents
Following the once assumed orientation (perceiving evil as a parody of good, interpreting the world’s history as strife between Tradition and Anti-tradition,
Children with various types of disabilities are beginning to benefit from the extensive developments in the field of electronic and microcomputer technology.. that have occurred
The cash derived from operations, before the refund for transaction costs, the Contribution from the Capital Fund Trust for net assets investment and the changes in operating
Delta file contains deleted rows within a given transaction range Data file contains rows inserted within a given transaction range. Data /
Thank you for agreeing to fill this questionnaire. The study is being conducted by a student of university of Nairobi SIMON MUNGU) to gather information about the effect
Third, our experimental design reveals that there is additional variation in expected work ability in East Germany, which cannot be linked to underlying risk factors and
Table 3b shows that when SENTIMENT is positive, monthly returns are 0.32 percent higher on profitable than unprofitable firms and 0.45 percent higher on payers than nonpayers..
The programs provide for actions that follow two main lines: the first emergency support with the distribution of winter equipment (mattresses, blankets, fuel,