Privacy in Cooperative Distributed Systems: Modeling and Protection Framework
Full text
Figure


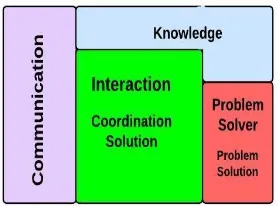

Outline
Related documents
By using stochastic method (e.g. the SFA, Stochastic Frontier Analysis), one may show the influence of external variable (the integration in the supply chain) on the
Outcomes of interest were differences in CT median income, age, BMI, and gender be- tween HRA and THA patients, as well as differences in CT median income, age, and BMI between
For every 100 additional users in a Fat-client Application we need only add 10 units of processing power to our server because we are utilizing the existing power of the desktop PC
As próteses auditivas adquiridas pelo Governo Brasileiro para a condução de políticas públicas têm como uma de suas características a utilização de componentes dedicados, o
On the basis of the studies carried out for some years by the author of this paper on the office space market in Pozna ń , it can be concluded that the above classification
The effects of written information of key sensory characteristics of apple cultivars on 7.. hedonic ratings and willingness to pay (WTP) were measured in an
As can be seen, simply assigning parameters from typical images for the three classes and performing a naive Bayes classification does not provide satisfactory results because
As noted above, the U.S. Air Force, Army, and Marine Corps currently do not require military engineers to obtain professional credentials before practicing. Instead, the decision



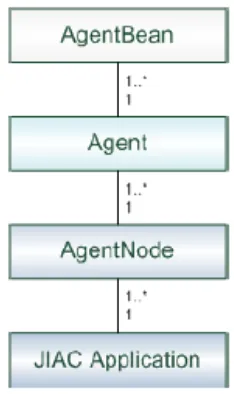
![Figure 11. Agent Life Cycle in JIAC Platform [28]](https://thumb-us.123doks.com/thumbv2/123dok_us/7767327.1277509/98.612.127.529.195.301/figure-agent-life-cycle-jiac-platform.webp)
