Analysis of Various tools of Penetration Testing Harshdeep Singh 1, Jaswinder Singh2
Full text
Figure

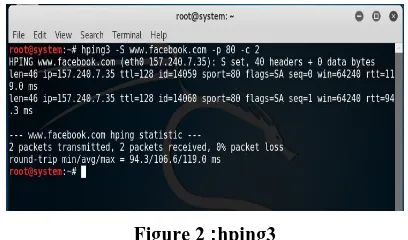


Related documents
Penetration Testing: Communication Media Testing covers Wireless Network Penetration Testing, Advanced Wireless Testing, VoIP Penetration Testing, VPN Penetration Testing,
At Caretower, we help businesses to identify vulnerabilities within their security systems and provide an action plan to help prevent security breaches occurring in the long run..
the response contains at least one record in its answer section, then the record is cached if it matches the entry in the query section, while NS records in the Authority section
Product Name: Security Testing Market by Network Security Testing, Application Security Testing, SAST, DAST, Security Testing Tools, Penetration Testing Tools, Automated Testing
A cloud can be private or public. A public cloud sells services to anyone on the Internet. Amazon Web Services today is the largest public cloud provider. A private cloud is
It is the process by which your data, and even your applications (your software and services), are moved online (i.e. away from your desktop) into the cloud, providing you and
Among the different land uses, the MMF model predicted the highest monthly splash detachment rates for barley fields with a total annual rate of 93.8 Mg ha -1 y -1 and a maximum
1. Cyber Security Assurance: to explore the various methodologies and techniques of penetration testing and cyber forensic in the computer network and ubiquitous system. Cyber