Investigation of the Exercise Dependence of Athletes Doing Kickboxing, Taekwondo and Muaythai
Full text
Figure
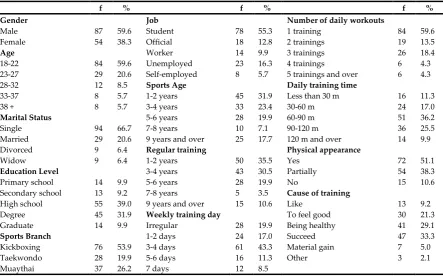
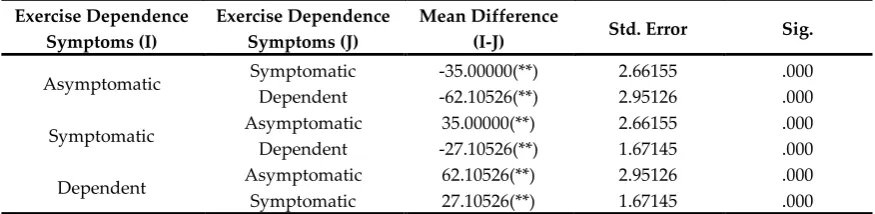
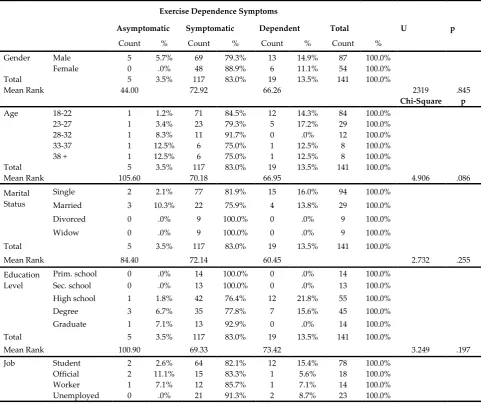
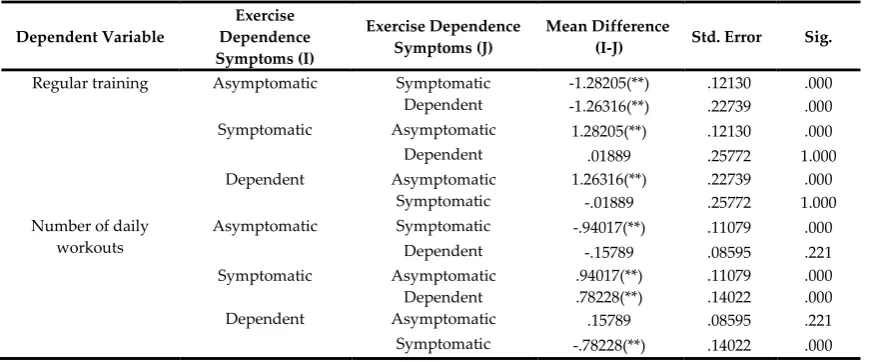
Related documents
- the application is submitted during the first and second enrolment phases. In the third enrolment phase this guarantee will be given provided that it does not entail the division
It is another anti-aging product that has a blend of vitamins that help to perfect the skin pigments, smoothes & minimizes enlarged pores.. This is one of those
We present a sampling-based approximation algorithm for the problem of finding the compact consensus shape from a family of proteins.. Our algorithm requires that the consensus
Force Composition 1 medium ’Mech regiment, 1 heavy aerospace fighter wing, 1 vehicle regiment, 1 infantry regiment, 1 artillery company; Third (’Mech) Battalion is light ’Mechs
During the process of cleaning up the patent database, six iberdrola entities have been identified: Iberdrola, Iberdrola Ingeniería y Consultoria, Iberdrola Ingeneria
Efforts include identifying adult learning needs; delivering new program opportunities in smaller communities, often collaboratively; engaging underrepresented learners in
We examine commercial vans and electric tricycles in three distinct phases: [I] vehicle cycle (from raw material extraction to disposal considering different vehicle
A drawback of this stream authentication scheme is that each receiver needs to store the key chain and packet in- formation to verify the packet authenticity.. While the key chain