A Review : Video Tampering Attacks and Detection Techniques
Full text
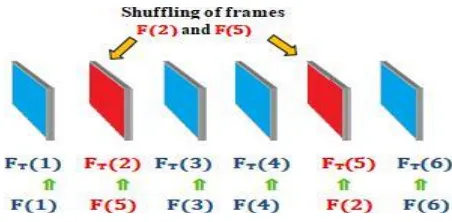
Figure




Related documents
The Arnold court found that the duty arises from the special relationship in the insurance context from the unequal bargaining power of the parties and the
We observed significantly more neutrophils in PICLC immunotherapy mice than in control mice at experimental day 0 (after receiving one dose of PICLC but before infection), but
We previously established in a HeLa cell model that infection with S-CDT-positive NTS strains activates a DNA damage response and induces an accumulation of cells in the G 2 /M
29 Although the trial court found that the landowners have access to a large supply of water for irrigation because the Brazos River now has many dams, 30 that
(court found minimum contacts even though foreign corporation delivered products indirectly into forum through independent distributor); Strick Corp. Thus, the liberty
As DapF CT appears to make use of the same substrate- binding pocket when carrying out both epimerase and racemase activities, we rea- soned that the enzyme’s active site
We showed that mosaic penA alleles found in Cro r clinical isolates are outcompeted by the Cro s parent strain in vitro and in vivo but that compensatory mutations that
A number of cases addressed the situation in which a party failed to list a witness in its response to a discovery request and then sought to introduce testimony