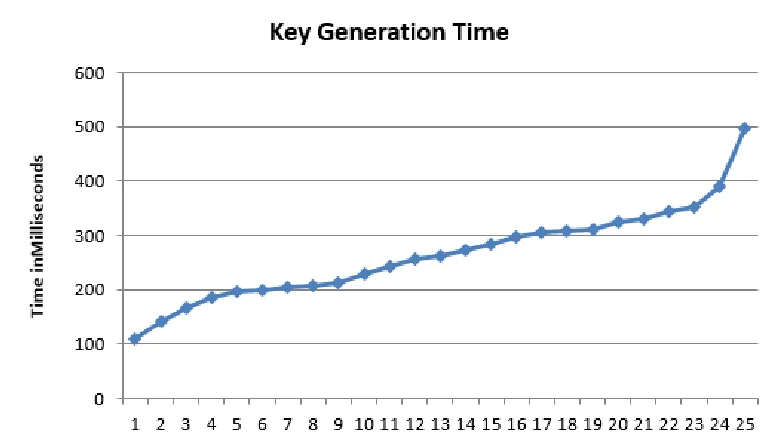
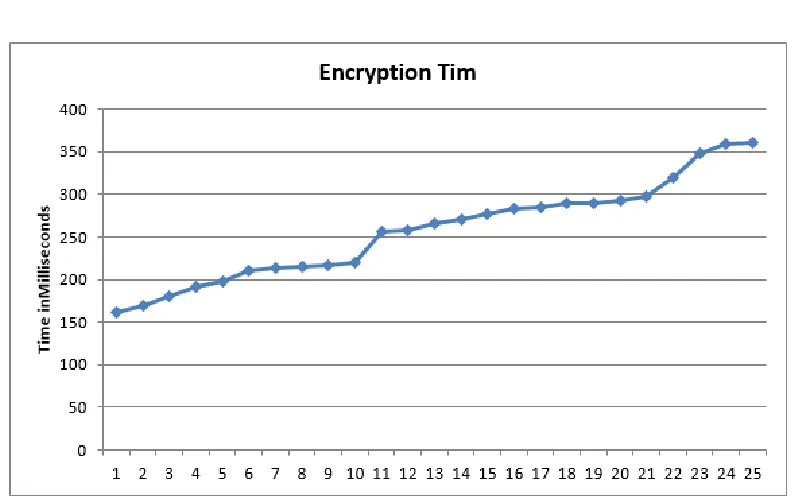
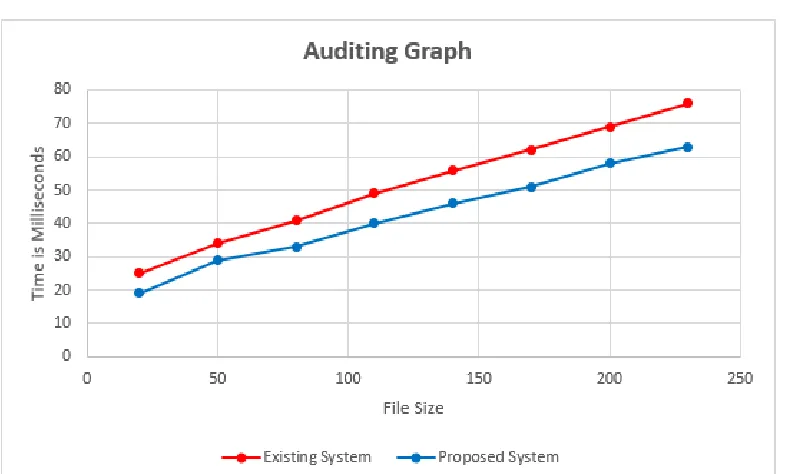
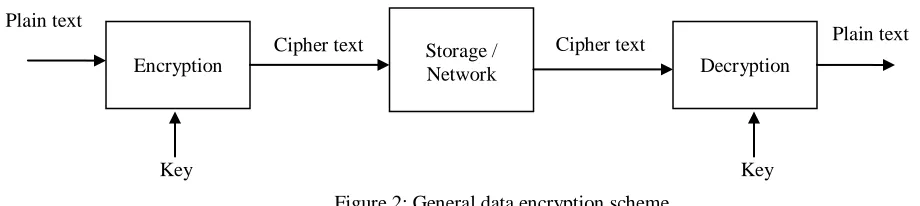
An Efficient Privacy Preserving Public Auditing Mechanism for Secure Cloud Storage
Full text
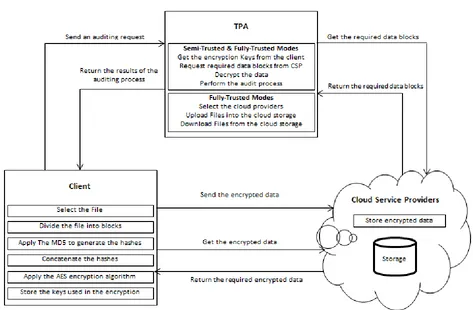
Figure


Related documents
ABSTRACT: The species belonging to the genus Ixora are amongst the plants in Indian traditional Ayurveda system of medicine for a variety of ailments. The research work carried
Machining parameters like cutting speed (m/min), feed per tooth (mm) and axial depth of cut (mm) are considered as input parameters and surface roughness and cutting
acts on a function g : [0, ) [0, ) (chosen from an appropriate class) playing the role of the local diffusion rate for the single components in the system. Therefore we had a
Many metabolic disease risk factors, including insulin re- sistance begin to accumulate in young adulthood [15]. Consequently, there is an acute need to establish a sensi-
Chapter 3 presents the developed Clustering and Differential Alignment Algorithm (CDAA) for gene regulatory connections inference from unevenly sampled whole genome time course
The Model is involved in the domain object, while the View is the actual interface that is displayed to the user, and the Controller is involved in handling the user input and
Before constructing any wrapper to extract the data on a web page understanding the html source code helps in building the better ones. HTML stands for Hyper Text