Data Exchange in Network File System Using Authenticated Key Exchange Protocol
Full text
Figure
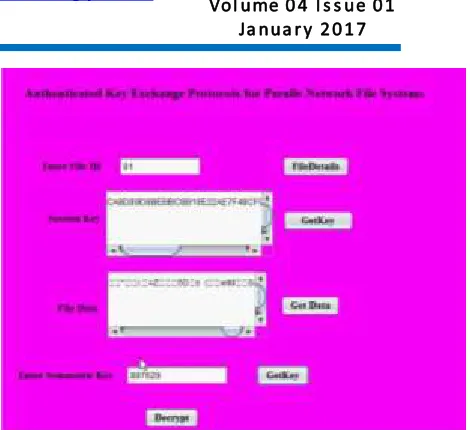
Related documents
Ray neuron function is compromised in tbb-4 , tba-6 , and tba-9 mutants: Because ciliary axonemes are gener- ally present in tubulin mutants, we asked whether these mutant cilia
In Panis Y et al study, in CDD group the cholangitis was secondary to sump syndrome in 3 cases, anastomotic stricture in one patient and unknown cause in 2 patients.. In our
While the previous work utilized both RGB and depth images for perception and motion. control respectively, two different python nodes took care of the two
The purpose of this qualitative case study based in Randolph County, North Carolina, is to determine whether AIM Clubs (middle and high school after-school clubs) can help
Loss of function bulge alleles suppress the rough eye phenotype associated with overex- pression of argos; conversely, amorphic argos mutations suppress the eye
Major results are as follows: (a) even the slightest migration removes the dependency of the final outcome on initial conditions, producing a unique equilibrium
(The four bases in.. We can generate se- quences that exhibit taxonomic exchangeability on the computer by choosing sites at random from the sequences of a group
So, we first characterize the possibility of URMT in arbitrary digraphs tolerating non-threshold mixed adversary, then describe the modifications needed to adapt the charac-