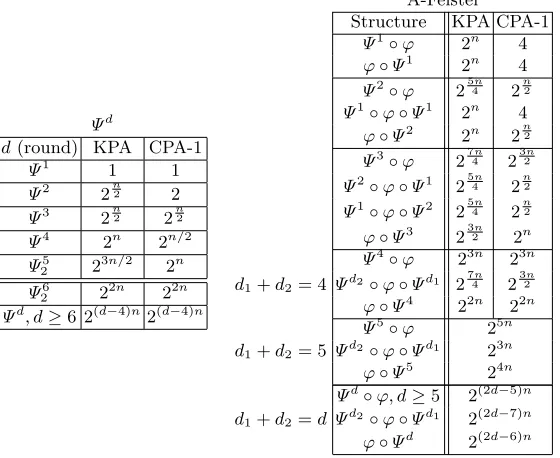
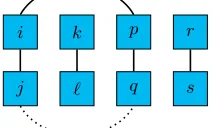
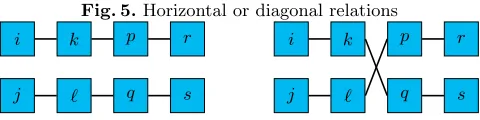
4-point Attacks with Standard Deviation Analysis on A-Feistel Schemes
Full text
Figure

Related documents
We also find that asset market risk factors such as exchange rates or stock market shocks affect the term structure of oil futures prices in a much more homogeneous way
If a Caller ID CO line is programmed to direct ring more than one station (81~89) a station logical port must be assigned as owner of the ground and/or loop start Caller ID line
field situations, these data indicate that a 10 C increase in cooling water temperature of a power generating stat.ion need not be lethal during spring migration of post-larval
The specific objectives of the study were; to establish the influence of employee training, continuous improvement and employee motivation and operational
By identifying one or more criteria to efficiently quantify and identify rapid tool wear, it can be determined when to change the tool and also Study tool wear effect by
Methodology: Sixteen prospectively studies have been performed using endoscopic ultrasonography-guided fine needle aspiration (EUS-FNA) in patients with submucosal hypoechoic
Numerical analysis has been carried out on a 1/13 th scale model of the DHX used in the CDA mock-up studies using the pressure distribution obtained form the mock-up study as
The WIQ analysis produced a seven factor structure (Working with Hardware, Clerical and Business Detail, Caring for Living Things, Scientific Activities, Artistic and
