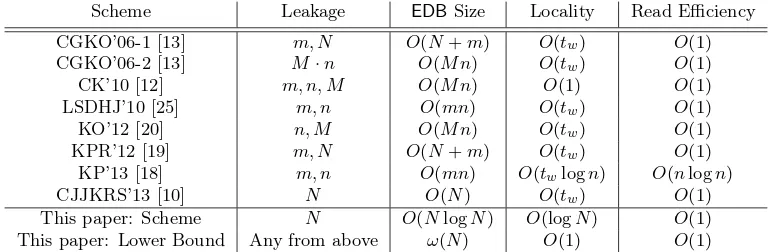
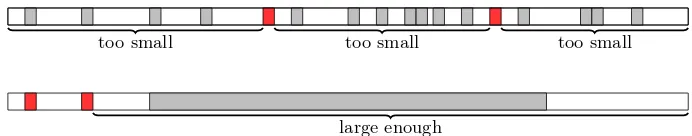
The Locality of Searchable Symmetric Encryption
Full text
Figure

Related documents
An analysis of the economic contribution of the software industry examined the effect of software activity on the Lebanese economy by measuring it in terms of output and value
This suggest that developed countries, such as the UK and US, have superior payment systems which facilitate greater digital finance usage through electronic payments compared to
In the Calculate Payout form, the “For each Commissionable Credit, type in calculations to determine the calculated Payout amount” radio option is selected to calculate the
were by right the emperors whom Christ and St Peter had commanded that all Christians should obey. The exalted nature of the emperor’s position was reflected in his
Sedangkan robot yang menerapkan fuzzy logic untuk wall tracking mencatatkan waktu yang lebih kecil, pada sampling jarang waktu rata-rata robot untuk memadamkan api
Inverse modeling of soil water content to estimate the hydraulic properties of a shallow soil and the associated weathered bedrock.. Ayral
The interdisciplinary components of the HeLP Clinic are multilayered, involving different activities and students from different professions� For example, fourth year medical
This study aims to research into whether the Taiwanese-Mandarin bilingual aphasic patients with the selective recovery pattern lose the knowledge of the inaccessible language or