Effect of Black Hole Attack and Prevention in Mobile Ad Hoc Network
Full text
Figure
Related documents
affect consumer demand for goods and services (Table 1). These spending differences generally ref lect the size, composition, lifestyle, and income of those
At the present time, according to the DSM-IV-TR 16 , in order to diagnose paedophilia it is necessary that, over a period of at least 6 months, the person presents
These include changing how C is allocated in fixed and dynamic schemes based on data from current forest syntheses and different parameterization of allocation schemes for
The ZKP is used to ensure non transmission of crucial cryptographic information in the wireless network in order to avoid man-in-the middle (MITM) attack and
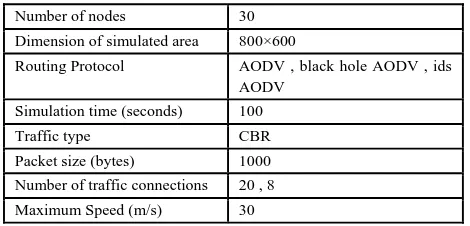
“Optimized Ad-hoc On Demand Distance Vector Routing Protocol[4]” explained that, A Mobile Ad-hoc Network (MANET) is a collection of wireless mobile nodes forming a
There has been sharp disagreement among courts about whether the IRC and FDCPA constitute applicable law under Section 544(b) of the Bankruptcy Code, such that the creditor
Here, we have shown that the novel ovine forestomach ECM scaffold material is cytocompatible to tenocyte cell growth, non-immunogenic and improves the histological appearance of
Keywords: Hospital-dependent patient, Acute care hospital, Length of stay, Palliative care, Hospitalist, Intensivist, Clinical ethics, Professional obligations, Role morality,