Vampire Attack: Solution using Energy Efficient Trust Value
Full text
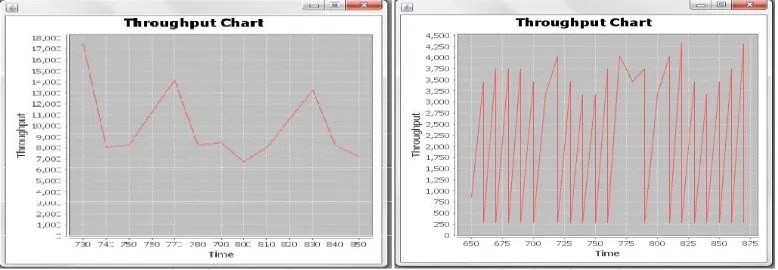
Figure

Related documents
Fu, “Measuring the Performance of IEEE 802.11p using NS-2 Simulator for Vehicular Networks,” in IEEE International Conference on Electro / Information Technology (EIT 2008). Van
In this section we formulate this problem as a Generalized Nash Equilibrium Problem (GNEP): Section 3.1 is devoted to the formulation of the SaaS resource allocation problem,
The University Grants Commission (UGC) is the apex organization for higher education in the country and is devoted to achieve the highest quality and world class standards in
In addition, Bracon, Hunt and Page (1994, 1995) completed the first com- prehensive hymenopteran genome mapping study when unlike honeybees, were easily mated in captivity.. In
In the present study showed the qualitative and quantitative analysis of the phytochemical constituents in the methanolic extract of the whole plant of Mollugo
Experimental study on the effect of welding speed and tool pin profiles on AA6082-O aluminium friction stir welded butt joints, International journal of
importance of these seven plant species to this territory is attested in the biblical description of the Promised Land that had been prepared for the Israelites: “For the
Let us investigate the influence of the buoyancy force of Archimedes, the forces of inertia of Carioles, the resistance force and the magnitude of the