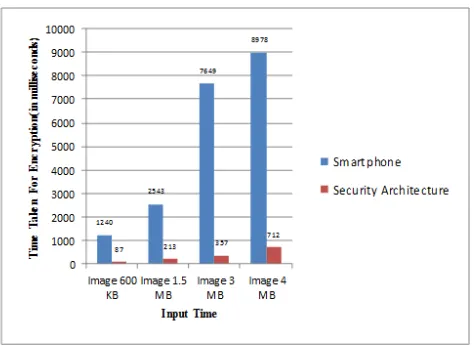
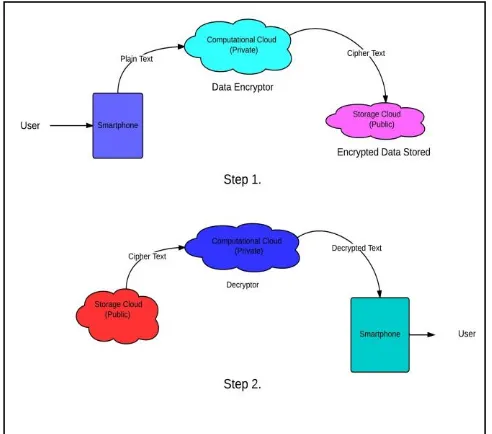
Securing Smartphone Data by Offloading Computation on Cloud.
Full text
Figure



Related documents
• Experience in developing naturalist education programs, California native plant propagation and community based restorations within the non-profit sector.. • Cris joined the
I have requested that this evaluation and recommendation form be completed by the recommender for the admission’s process by the Admissions Committee in the Department of
For those in the computer security, networking, and telecommunications industries, sponsorship opens the doors to a highly influential community of computer security incident response
By pre-empting my recommendation in the next chapter on the creation of outer islands shipping network system; the implementation part of that proposal would be as follows; That
To address this, the JISC Usage Statistics Review Project aims to formulate a fundamental scheme for recording usage data and to propose a standard for its aggregation to
For palatal, maxillary buccal and mandibular insertion sites, data were eligible for pooling if two or more studies reported the failure rate for a specific inser- tion site..
Table 9 presents the estimates of the labor market returns to speaking a foreign language using college and high school graduation requirements as instruments for the ability to speak