Secure Authentication Framework in Wireless Sensor Networks
Full text
Figure
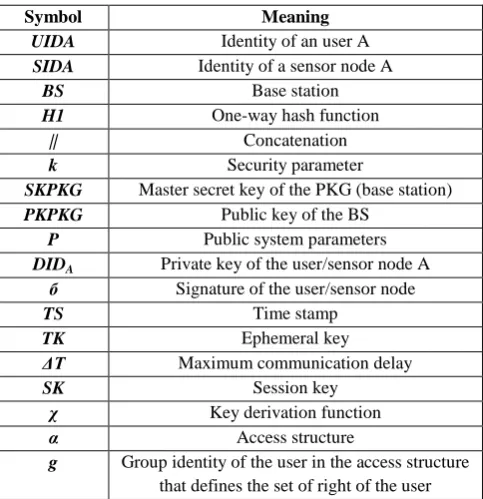
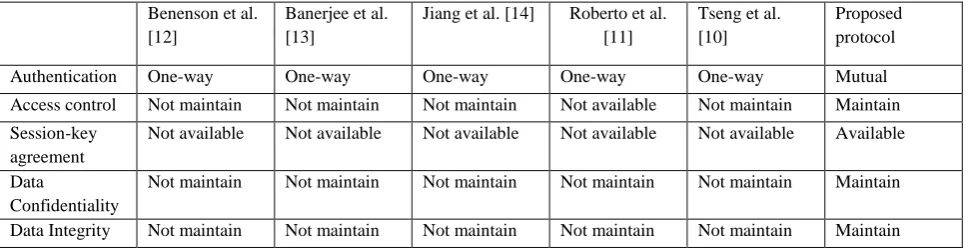
Related documents
The sensitivity of oogenesis to gamma rays depends on the reactivity level: After irradiation, the medium reactive flies (By) exhibit good fecundity and the lowest
These results reveal that gene introgression at the DNA level from the upland cotton may contribute to the increases in conductance attained in advanced introgressed pima breeding
Moazzami, ”T-sets and its Properties in Stability Calculation”, 23 rd South In- ternational Conference on Combinatorics, Graph Theory and Computing, February 3-7, 1992 at
Currently, the only studies that include these e ff ects in rapidly rotating stars are those based on [80], which use models based on a Chandrasekhar expansion and focus on low
signify the positive responses of foreign reserves to portfolio inflows shocks, Korea, Thailand and a group of economies with floating regime do not show any responses of
CHAPTER 2: ALLOCATION PATTERNS, LIFE-HISTORY TRADE-OFF, AND RELIABLE SIGNALLING IN CAROTENOID-BASED ORNAMENTATION IN MALE REDSIDE DACE
Keywords: High-risk pulmonary thromboembolism, Fibrin-rich thromboemboli, Percutaneous mechanical thrombectomy, Open embolectomy.. *
Keywords: Evaluation, Staff’s Performance, Job Satisfaction, Organizational Commitment, DEA, Khuzestan Oxin Steel Company.. Corresponding Author: