Person Authentication using Iris Recognition
Full text
Figure
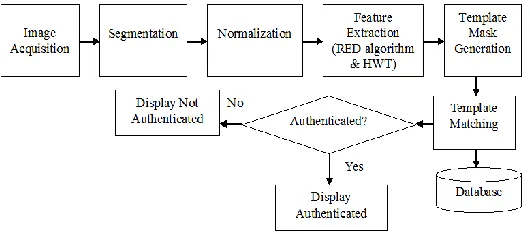
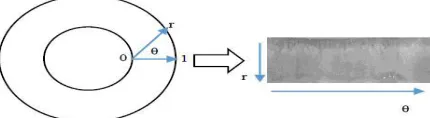
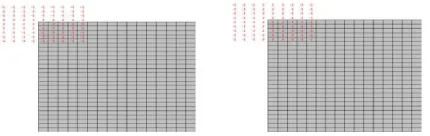
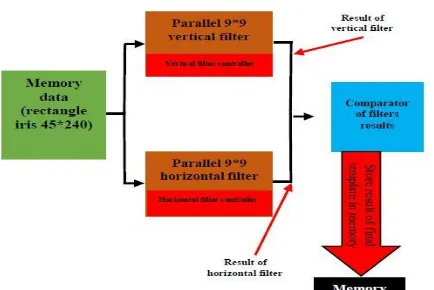
Related documents
The indexes are arranged alphabetically by surname in groups of 25 years and are microfilmed copies of typed cards compiled by June and Richard Ross of Redlands, California, filmed
However, this premises the existence of efficient tools that are not restricted by the high computational burden of graph algorithms as all-pairs shortest path (APSP) computation
The combined products and services of the successful acquisitions of Cambridge Energy Research Associates, Global Insight, SRI Consulting, Harriman Chemsult and Chemical Week
4 scholarship must examine the intersections of four interpretative strands: (i) the political construction(s) of food banking, particularly the enrolment of food banks
Maternal asthma, as compared with no maternal asthma, during pregnancy was related to an increased risk of a wide range of diseases in the offspring during childhood,
To the author’s knowledge, Milton (2008) is the only study that has investigated intentional vocabulary learning from watching films with subtitles. He carried out a